To continue the MSE Blog Series, I’m going to take you on a journey to dig deep into one of the features of Release 7.4, wIPS!
With the increasing popularity of BYOD, wireless security has become an eminent concern for Network Administrators. Cisco Unified Wireless Intrusion Prevention Solution (WIPS) is dedicated to protecting the wireless network security and provide a secure wireless experience to the clients. Cisco, allied with Flukes Networks, to constantly monitor new wireless intrusion techniques, develop new signatures and provide preventive solutions. In 7.4 release, we added the capability of detecting 802.11 frame fuzzing attacks. The new signatures patterns, for detecting such attacks, are available through WIPS profile configuration in NCS. These signature patterns are enabled by default and provide the full level of security. The user, however, could tune them to get the desired protection level.
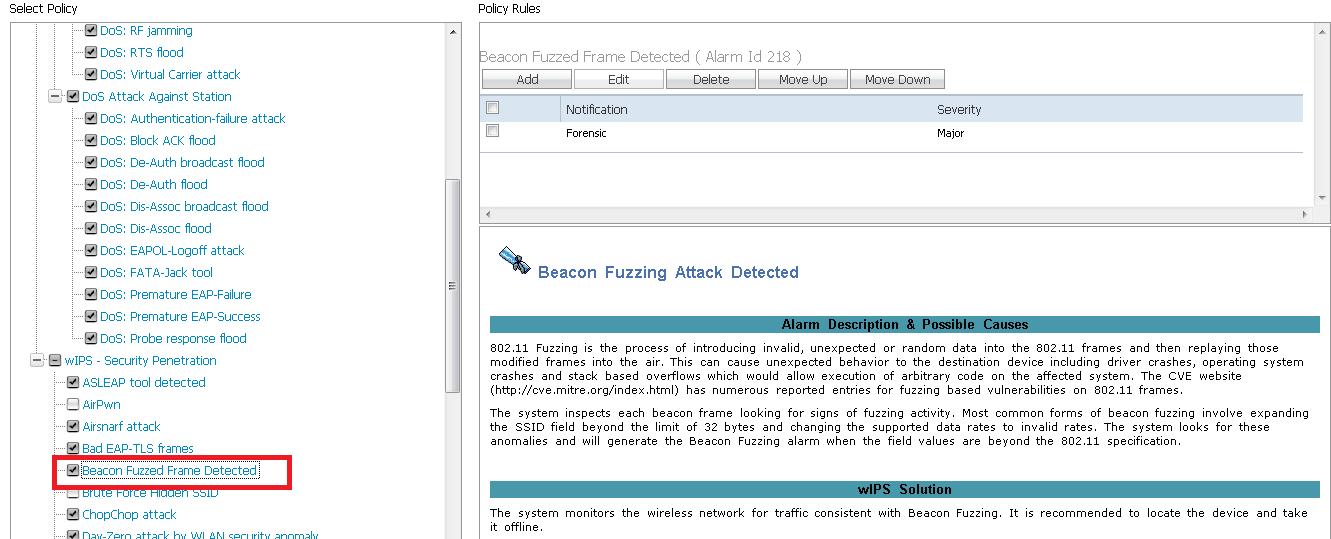
802.11 Fuzzing is a malicious security penetration attack which could make substantial damages to the victim devices. In these attacks, the attacker injects unexpected data into the 802.11 frames and causes the victim device driver/operating system to crash through stack-based overflows. These attacks, can basically render a device useless. With the new features in 7.4 release, Cisco customers can heave a sigh of relief and not worry about the fuzzing attacks.
We have also improved the features of the Enhanced Local Mode (ELM) in WIPS. ELM offers WIPS capabilities on a local mode AP that could detect about 85% of the signature attacks in comparison with a Monitor Mode AP. Now, in 7.4 release, ELM AP has reached parity with Monitor mode AP and can detect all the signature attacks that a Monitor mode AP can detect.
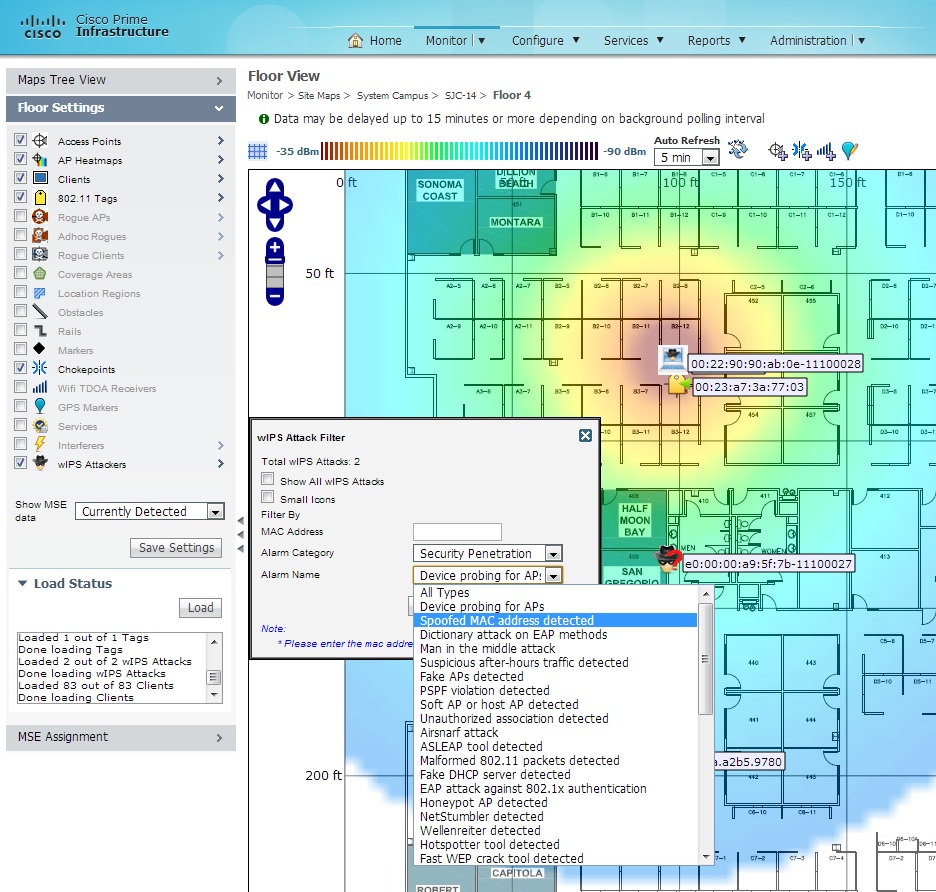
From the attack mitigation end, we have added new threat mitigation actions. When an attack is detected, user often wants to know what’s happened and what I could do to stop it and protect my network. While viewing the details of an attack, the user can take mitigation action, which is just a click away. Our mitigation methods range from automatically locating the attacks on a map to launching a corrective action by WLAN. MSE can pinpoint the physical locations of most of the wireless attacks. With the location information, the network administrator could remove the offending devices from the premises.
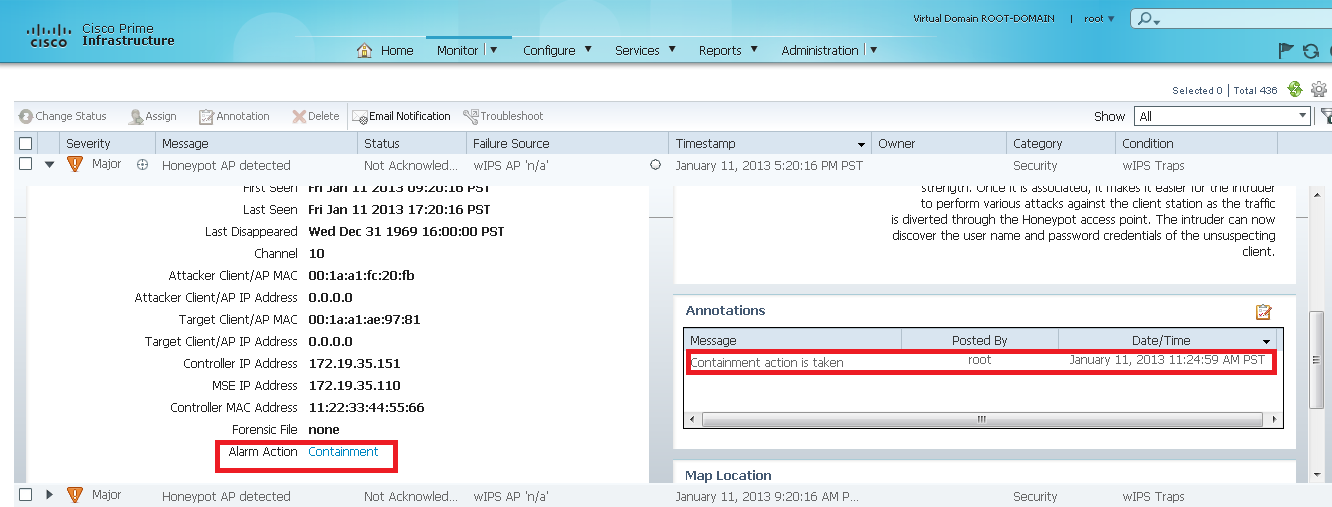
Containment action is made available for a selection of wireless attacks which involve Rogue AP/Rogue client activities. By issuing containment action, the attacker’s WiFi connection will be disrupted. As the result of the action, the attack will not be able to continue.
Also, for certain alarms, user could issue a blacklist action. Blacklist action adds the attacker device to the blocking association list, so that the device could not associate with the managed wireless network.
We put wireless threats on high visibility to give you the highest protection and mitigate detected attacks to enhance your troubleshooting experience. We are committed to improve user experience and would love to hear back from you.
For more on the MSE and Connected Mobile Experiences, visit our product page and solution page. We’re also taking questions on our community.


Very informative article post.Really looking forward to read more. Really Great.