 This post is coauthored by Andrew Tsonchev.
This post is coauthored by Andrew Tsonchev.
Anyone can purchase an exploit pack (EP) license or rent time on an existing EP server. The challenge for threat actors is to redirect unsuspecting web browsing victims by force to the exploit landing page with sustained frequency. Naturally, like most criminal services in the underground, the dark art of traffic generation is a niche specialty that must be purchased to ensure drive-by campaign success. For the past year we have been tracking a threat actor (group) that compromises legitimate websites and redirects victims to EP landing pages. Over the past three months we observed the same actor using malvertising – leveraging content delivery networks (CDNs) to facilitate increased victim redirection – as part of larger exploit pack campaigns.
Using Indicators of Compromise to Reconstruct Malicious Campaigns
Threat intelligence and incident response rely on triggers and anomalies to initiate deeper investigations. Two weeks ago, TRAC detected victim web redirection to a Styx exploit pack which uses common landing page JavaScript. We further confirmed that the malicious redirection activity was part of a larger ongoing campaign.
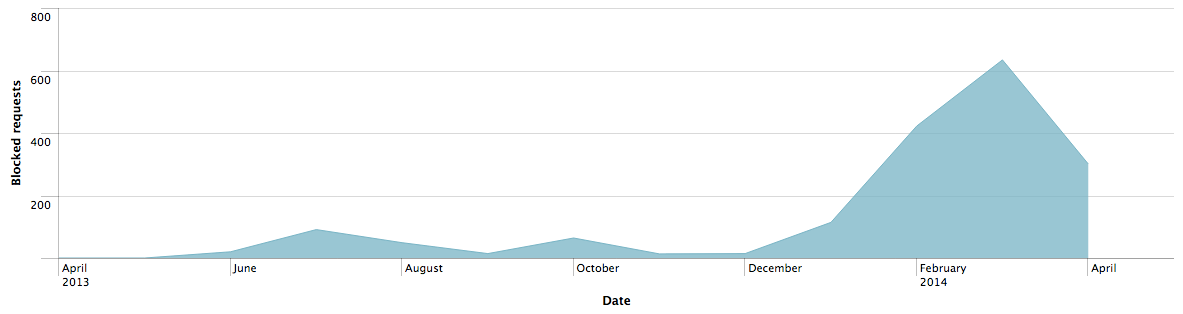
On April 1st, 2014 we began blocking specific malicious web requests from 256 users in 186 companies. The requests were destined for the following thirteen domains (which we label “stage two domains”), all of which resolved to 77.245.75.237 (Redstation Limited – Dedicated Server Hosting, Great Britain). The following stage two domains represent the final phase of the attack, but it was only the beginning of a lengthy historical incident response trail.
ovcn.drinkstablesflowws.us
gebm.medicksflowertype.net
hcg.onimevideosfloss.us
hnrf.drinkstablesflowws.us
mc.googledrinkcs.net
nckjf.medicksflowertype.net
nyjsz.drinkstablesflowws.us
prkun.googledrinkcs.net
qluht.medicksflowertype.net
tcyu.drinkstablesflowws.us
uhofz.medicksflowertype.net
vohx.googledrinkcs.net
xyl.medicksflowertype.net
Example of a full EP landing page URI for each of the above (stage two) domains:
/0BD3-Gr0D5-4417_g1I0-Vhk30vc_li0t-3G30bn6-M0B4Un-0URJ_j0ByWy0b_THP/08L/HG0KFU/J164A00PKj/m0Cf_ol0VWk_p13ER702f-Lv0f1j-j08_lYt04-WHQ0_FZrL/0KEf-70e/xy5/0gDYM0Gsn_h0BmFr_0WY1_50X2U/F05/f0W_0bKXG034_Sz130fC0_5mB_808n8-J0ol/ov0JpF_Y0e1g20/w5st1-4nxu/12MUS0RP/zc0Rr-O817d/VC/0GMkB0m_AeZ_0lq-T50y_AzI0Em-0F-0sccB-0buQ/Q0mJiy/0bie/v0eiLr-0lk_jI02/rHX/
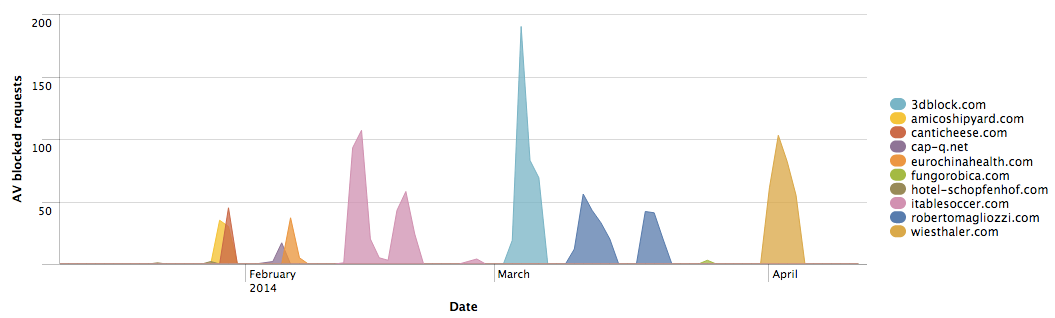
We subsequently extracted the referrers (“stage one domains”) that had driven our customers to the blocked exploit pack domains. The chart below depicts the stage one compromised domains and their rise and fall over time in the traffic that Cisco blocks due to increased bad reputation, at which point the threat actor(s) switch to using different compromised domains. Throughout this campaign the URI path – /b/728×90.jpg – remains constant regardless of domain. We observed this remarkable consistency for more than a year (with a few examples appearing as long as two years ago), making it a predictable indicator of compromise (IoC). Attempts to manually sample this specific file from compromised websites resulted in a variety of widely distinct artifacts; though the file name indicates a JPG image file, most artifacts only contain HTML that references additional external files. The 728 x 90 pixel specification is a common web page advertising banner size, possibly indicating a specific malvertising path, which also makes it difficult to detect malicious use in web server logs.
The specific attack that began on April 1st overwhelmingly affected victims in Great Britain. The exploit MD5 hashes differed for each victim request, as observed in a sampled list of Java Archive (JAR) files, and Styx likely dynamically generated the file for each victim request. Additionally, our manual HTTP requests to the EP landing pages above resulted in a 402 response code, which is unusual given that it’s designed for “Payment Required” and is reserved for future use. The 402 response may be another effective Styx IoC for future detection.
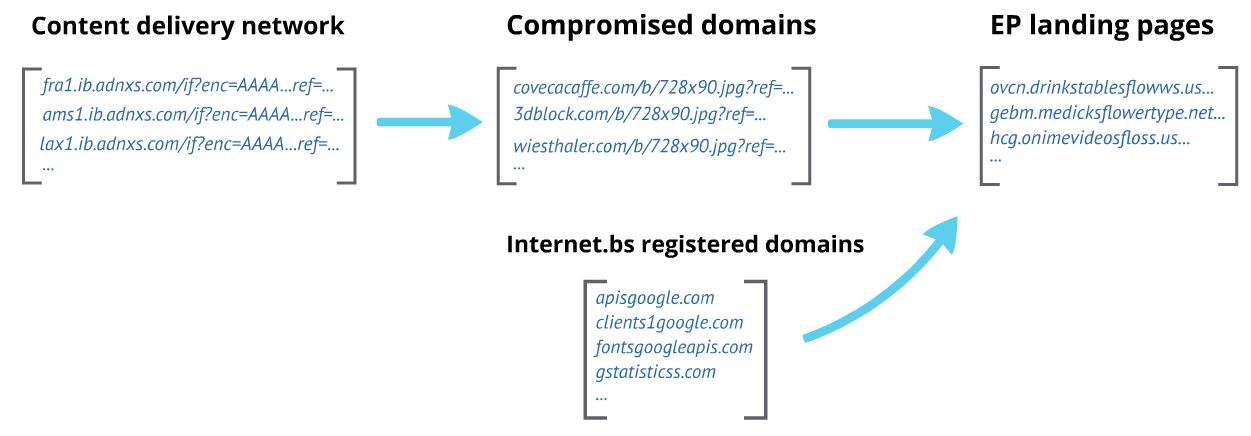
Working backward from the EP landing pages, there were two different types of referrers that transitioned from the stage one domains to the EP landing pages: redirections from a CDN through compromised sites and redirections through domains registered at internet.bs, a Bahamian registrar:
The first type of referrer was legitimate websites that had been compromised.
wiesthaler.com/b/728x90.jpg?ref=bestin fungorobica.com/b/728x90.jpg?ref=coolin robertomagliozzi.com/b/728x90.jpg?ref=newpub
In these cases, we observed the original redirection trail beginning from ib.adnxs.com to stage one domains. Thus, stage zero began in the adnxs.com CDN, stage one included redirection from compromised websites, and finally the EP landing pages were stage two. The convoluted redirection chain allows threat actors to tightly control which victims are exploited. If the referrer chain is broken, often the EP landing page will not attempt exploitation and instead serve a benign page, making it more difficult for researchers to obtain the actual exploits being used.
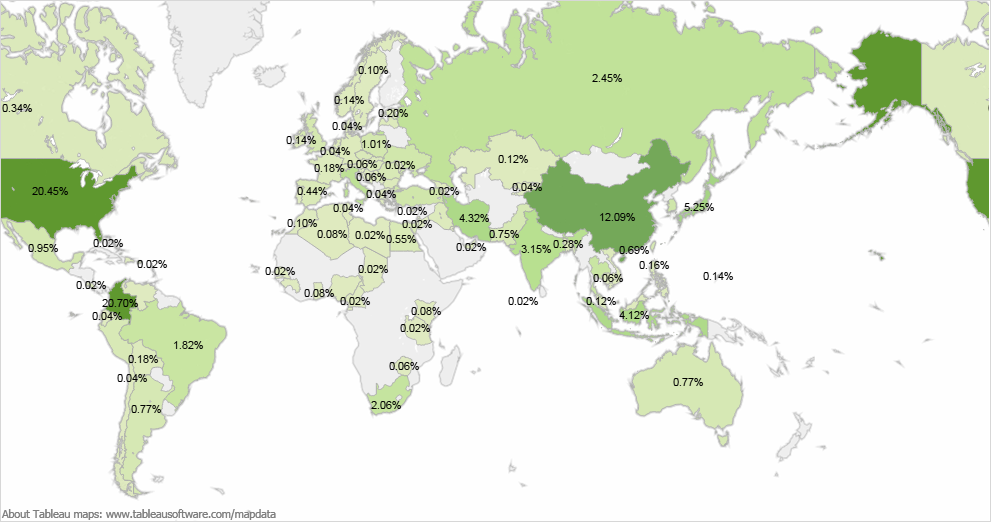
The second type of referrer was newly registered domains (late March – early April) that appear, at least by naming convention, to be disguising themselves as legitimate Google services. The list includes:
apisgoogle.com
clients1google.com
fontsgoogleapis.com
gstatisticss.com
gstatss.com
partnergoogleadservices.com
All of the domains are registered with internet.bs (.bs is the Bahamas’ top level domain (TLD)):
Registrant Name: Internet.bs Corp.
Registrant Address: 98 Hampshire Street, N-4892 Nassau — Bahamas
DNS Information: {ns1.internetbs.net, ns2.internetbs.net, ns3.internetbs.net, dns3.internet.bs}, {216.67.232.70, 77.247.183.97, 80.83.120.225, 76.191.252.194}
Expiration Date: 12-12-2014
Last Updated: 12-12-2003
Administrative Contact: Marco Rinaudo, marconicbs@rinaudo.com, 327 24 88
Internet.bs was also used to register the domain – pphnq.downsdlowerscars.com – that acted as a Styx landing page for visitors to Hasbro’s website (after the site was compromised in January).
The registrant(s) for each domain used Internet.bs’ associated Panamanian Privacy Protect service:
Registrant Organization: Fundacion Private Whois
Registrant Street: Attn: partnergoogleadservices.com, Aptds. 0850-00056
Registrant City: Panama
Registrant State/Province:
Registrant Postal Code: Zona 15
Registrant Country: PA
Registrant Phone: +507.65967959
Name Server: ns-canada.topdns.com
Name Server: ns-uk.topdns.com
Name Server: ns-usa.topdns.com
App Nexus owns adnxs.com, which appears to be a specialized advertising CDN. When we attempted to email abuse@adnxs.com for information related to this campaign, we received notification that email delivery was unsuccessful due to Cisco’s internal Response Policy Zone (RPZ). Further investigation revealed that all adnxs.com requests were sinkholed due to reputation based on previous malware events. Next, we called App Nexus and asked for an abuse contact and were redirected to a representative’s voicemail where we requested a call back to discuss this particular malware campaign. In the meantime we explored prior malware tied to adnxs.com over the past four years.
We are aware of 511 malware samples tied to cdn.adnxs.com and 7232 malware samples tied to ib.adnxs.com. Obviously malware often connects to legitimate companies like Google to check Internet connectivity from a victim host, and in this case malware may be leveraging the App Nexus platform for click fraud purposes. Analysis of the first sample in the ib.adnxs.com list reveals malware that is performing DNS A record requests for ib.adnxs.com followed by HTTP GET requests.
sha1: 03f3e8b12963b6d9f59dd0c80c032c6db349b8ad
md5: 2131254aec2869d5cefc7eaa09a1d76a
filetype: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
size: 1755386
packer: BobSoft Mini Delphi
anti-virus labels: Trojan:Win32/Neop, Trojan.ADH, Trojan-Dropper.Win32.Mudrop.way
mutex: Iexplore.XPExceptionFilter
HTTP Get: hxxp://ib.adnxs.com/ttj?ttjb=1&bdref=http%3A%2F%2Fcongdonghackgame.forumvi.com%2F&id=1092879
HTTP Get: hxxp://cdn.adnxs.com/ANX_async_usersync.js
icon:
![]()
We are aware of at least 647,821 samples that use the same mutex – Iexplore.XPExceptionFilter – and 56 samples that use the same icon. As the mutex indicates, this malware spins up new Internet Explorer processes, related files, and registry keys.
C:\WINDOWS\system32\ieframe.dll
C:\WINDOWS\system32\urlmon.dll
C:\Program Files\Internet Explorer\IEXPLORE.EXE
C:\WINDOWS\system32\en-US\ieframe.dll.mui
C:\Program Files\Internet Explorer\IEXPLORE.EXE -nohome
C:\Program Files\Internet Explorer\iedw.exe -h 1364
C:\WINDOWS\system32\dwwin.exe -x -s 1428
After executing the sample, the packet capture (PCAP) reveals traffic to multiple sites and networks, primarily congdonghackgame.forumvi.com.
GET / HTTP/1.1
Accept: */*
Accept-Language: en-us
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Host: congdonghackgame.forumvi.com
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Sat, 05 Apr 2014 06:55:15 GMT
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: keep-alive
P3P: CP=”IDC DSP COR ADM DEVi TAIi PSA PSD IVAi IVDi CONi HIS OUR IND CNT”
Cache-Control: no-store, no-cache, must-revalidate
Cache-Control: post-check=0, pre-check=0
Expires: Sat, 05 Apr 2014 00:00:00 GMT
Last-Modified: Sat, 05 Apr 2014 06:55:15 GMT
Pragma: no-cache
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Encoding: gzip
Successfully Monetizing an Exploit Pack Campaign
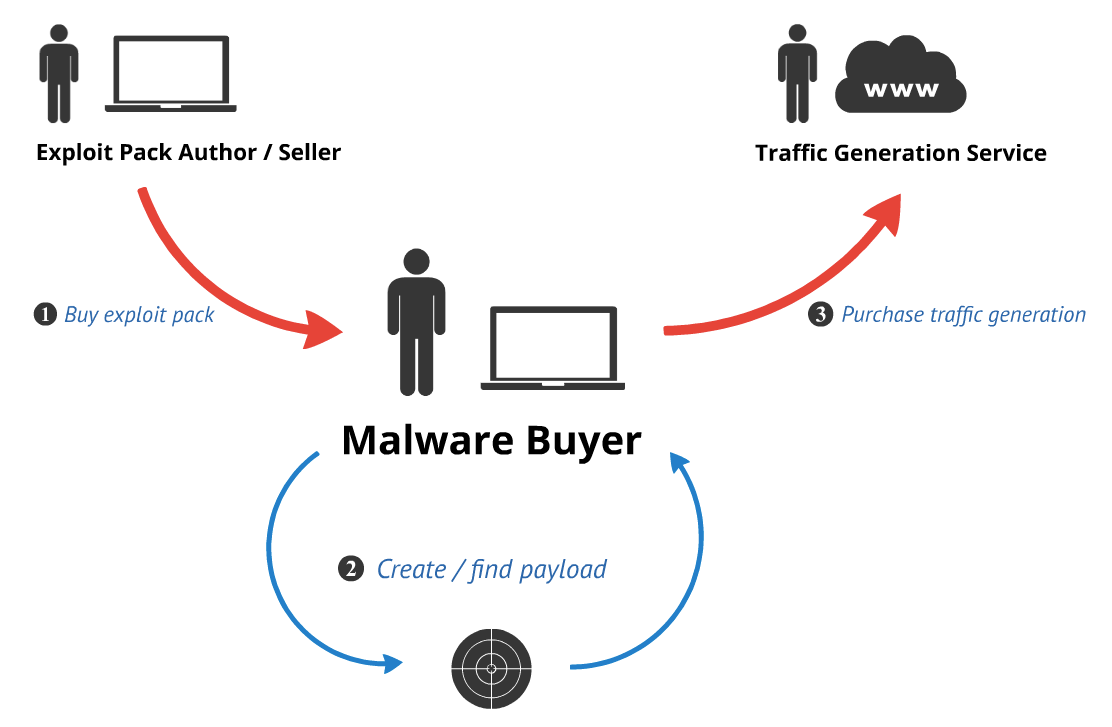
As illustrated in the image below, once a threat actor purchases access to an exploit pack, the subsequent steps in a successful drive-by attack include providing a malicious payload to insert into the EP configuration, and finally redirecting unsuspecting web browsers to the EP landing page. There are a number of ways to redirect users, and in this campaign a CDN was used in conjunction with legitimate website compromises.
In the most recent attack campaign, Styx was the payload delivery and monetization mechanism designed to create hordes of victims, but we also observed the same web traffic redirection vehicles being used to force web browsers to different EPs (including Neutrino) over the past year. The full list of adnxs referrers, compromised legitimate websites using the same URI path (/b/728×90.jpg), and EP landing pages creates a harrowing narrative for web users.
CDNs are attractive targets for threat actors to seed malware, redirect users, and/or check connectivity status on a victim machine because the CDN is a preexisting platform that maintains relationships with some of the largest websites in the world and thus instantly reaches millions of potential victims. Obviously it’s incumbent upon CDNs to monitor and police their network to prevent malvertising, which App Nexus may not currently be doing based on the malware numbers and relapsing drive-by campaigns that originate from adnxs.com.
Individuals can protect themselves from initial malvertising redirection via web browser add-ons like No-Script that will prevent third party content (JavaScript, cookies, advertisements, etc.) from rendering on a first party website without explicit manual approval.
About the Styx Exploit Pack
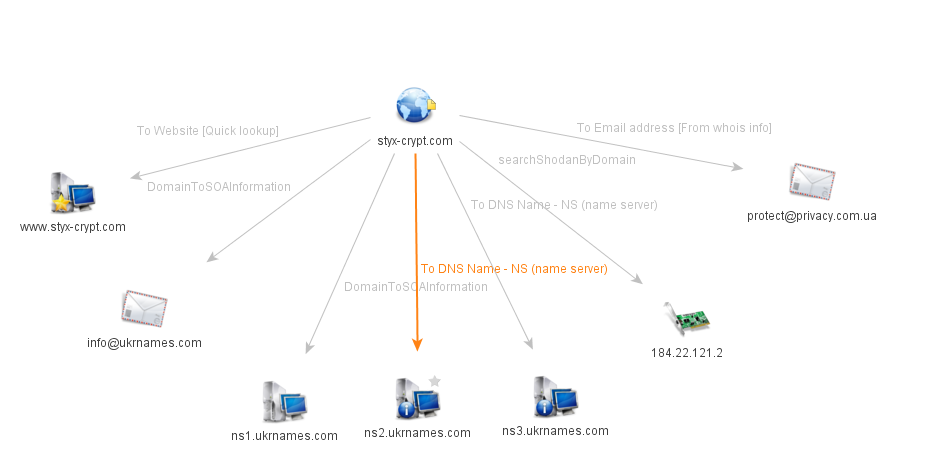
Styx is an exploit pack that gained notoriety in 2012 when it was heavily advertised in various criminal web forums. This particular exploit pack is notable because the author(s) brazenly created a website – styx-crypt.com – providing detailed information about the EP and its exploit efficacy. The following is one such 2012 advertisement:
We have some great news for you now. Styx Sploit Pack. Gentelmen, it’s a time to announce a new next generation product for private customers: Styx Sploit Pack. Our team worked hardly around two years to make a quality product which will be trustful for any person. Also we made a deep testing so this product already tested with our crypt. Frequently asked questions:
The styx-crypt.com domain still resolves to an IP address though the website is currently offline. The domain registrant’s email address uses a Ukrainian privacy protect service and the name servers are also located in the Ukraine.
Conclusion
As documented in Cisco’s 2014 Annual Security Report, cyber-crime attacks are still monetizing the end point, and increasingly, core Internet infrastructure is being leveraged to launch and scale these attacks. Web hosting is one such resource that is frequently stolen and misappropriated for exploit hosting and victim redirection in large swaths, making attack attribution increasingly difficult. Likewise, malvertising relies on CDN owner complacency, and when threat actors combine stolen server resources and malvertising, the standard Internet trust model suffers. Unfortunately, exploit packs and larger drive-by attacks will remain a continual threat until core Internet resources become difficult to purloin.
Indicators of Compromise (IoC)
Stage Zero – Adnxs.com – URI List
Stage One – Legitimate Websites – URI List
Stage Two – EP Landing Pages – URI List
Malware Associated with cdn.adnxs.com (MD5)
Malware Associated with ib.adnxs.com (MD5)
Sourcefire IPS Signatures
Styx Exploit Pack signatures (further details can be found by searching Snort – http://www.snort.org/search)



CONNECT WITH US