Everyone has a spam folder. It’s often disregarded as a dark, bottomless pit for fake emails from FedEx, pharmacy offers, and introductory emails from women far too amorous to be anything but fantastical. You’d be right to largely ignore this folder.
Yet each day new emails end up in it. Most of us have learned to leave it well enough alone. Still, few would admit to having no curiosity as to what’s in there. To satisfy this curiosity, we’ve dug into spam folders to explore the current types of messages being sent and find out what happens if you click the links and open the attachments. In essence, we’re opening these spam messages so you don’t have to.
Do not try this at home
This exploration is meant to inform, showcasing some of the scams and threats currently out there. However, in all of the spam messages we’ve examined, the links were clicked and attachments opened within a secure, sandbox environment.
In this case we used Cisco Threat Grid, which is an advanced sandboxing tool that can analyze threats against millions of other samples to fully understand its behaviors in a historical and global context, and then provide context-rich analytics and threat intelligence. We’ve also coupled this with Cisco Umbrella Investigate, which provides an excellent view of the relationships and history of particular internet domains and IP.
While most of the spam we looked at was prosaic, many were not. It’s mostly the latter that we’re showcasing here. Opening these emails on your own computer or device is very risky and can end up compromising it. In short, do not try this at home.
Snake oil sales
Let’s start off with the more mundane spam emails—the ones that more often than not simply attempt to part a fool from their money.
If there were a unified theory of spam it would be that it plays to both our aspirations and our insecurities: get in shape, lose weight, get a great night’s sleep, get the girl/guy, protect your family, improve your credit score, etc. There’s a wide variety of these emails that play to these desires—far too many to cover in any detail. Consider these as a smattering of what’s currently out in the spam landscape.
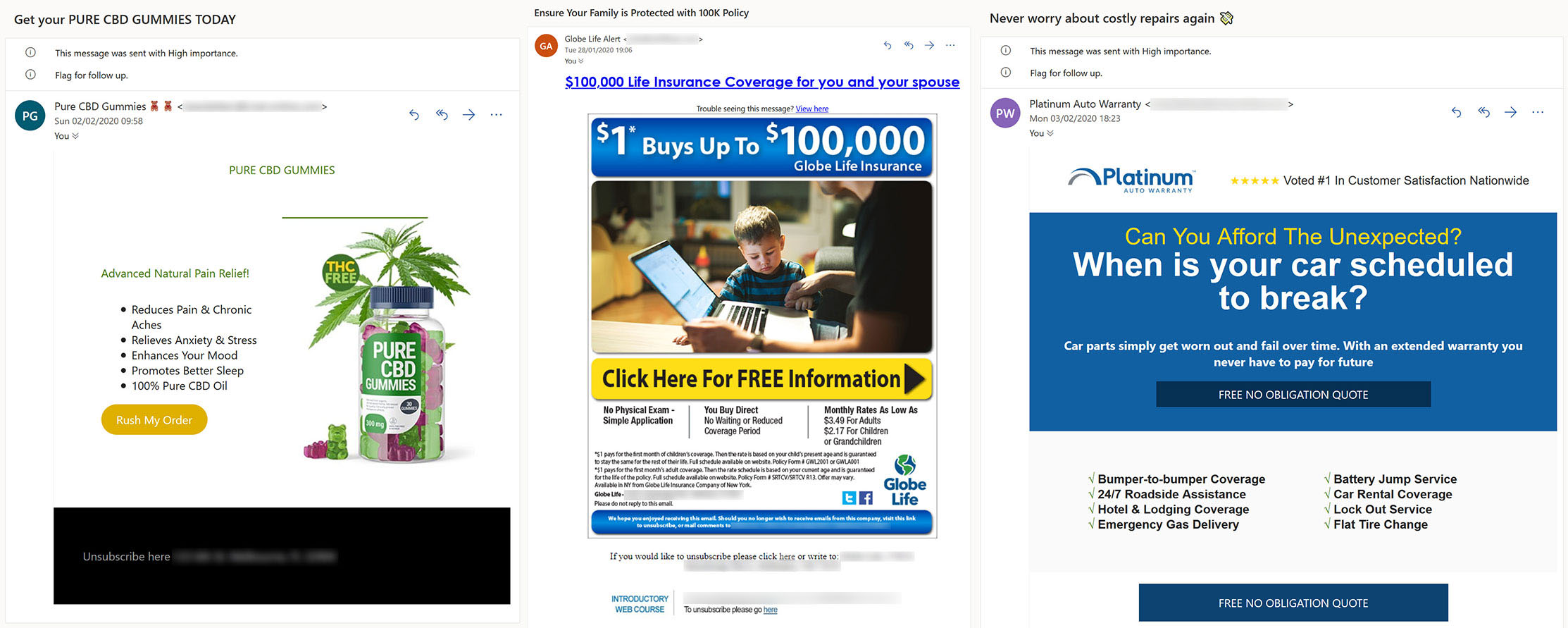
In this type of spam messages, many of the message bodies share similar characteristics. This points to the use of email spam kits that leverage templates for crafting emails. These kits go far beyond the email bodies too, allowing all sorts of customization. For instance, some of the examples above were marked as “high importance” and flagged for follow-up before they even hit the spam folder.
Text only spam
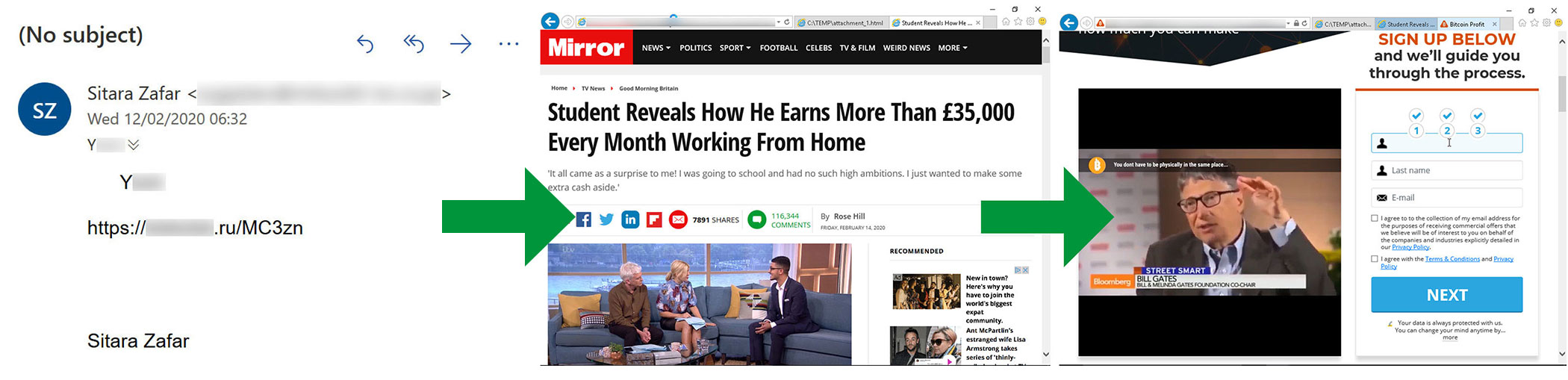
Sometimes saying nothing is more effective than saying anything at all. That’s certainly the case with spam, as bare-bones spam messages are very popular. For instance, some emails just put the recipient’s name in the body, along with a link. The link leads to a get-rich-quick scheme in the guise of a fake news report about a Bitcoin investment platform. A “Try Now” link on the page leads to a second site that gives the user an option to register.
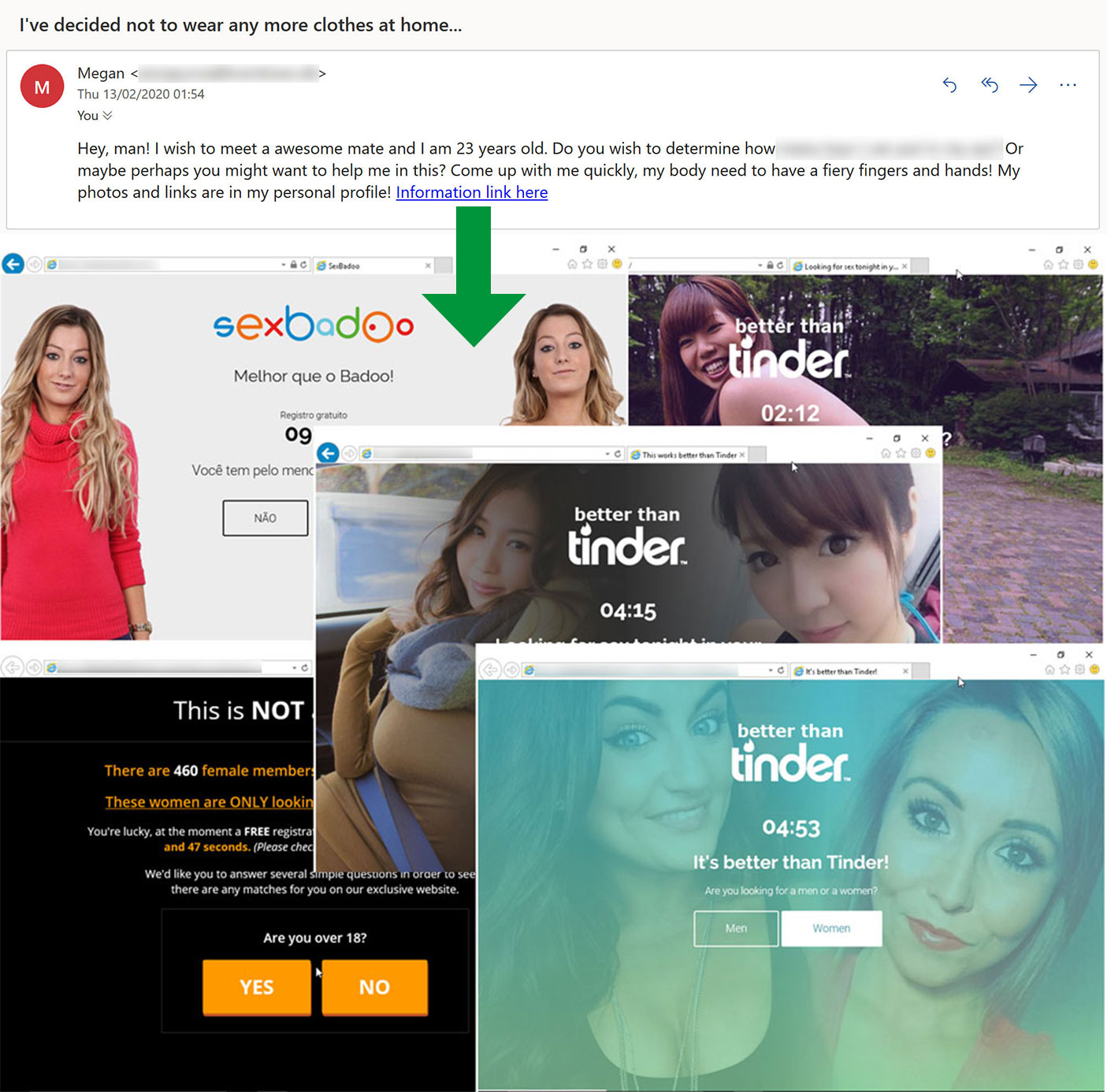
Spam promising romance or intimate encounters with strangers is also very common. Many are clearly advertisements, while others are attempts to begin a rapport before asking the victim for money. In this case, the site that you are directed to depends on the country you’re visiting it from. In general, these links guide users to lesser-known dating and meet-up sites, where it’s likely the scammers are generating ad revenue through click-through programs.
Social networking spam
Likes, comments, and profile views are the lifeblood of social networking, and the networks often entice users to return to their sites by sending emails on the user’s profile activity. In this particular example, the scammers have lifted the look of a LinkedIn email notifying the user that their profile had appeared in searches. If any of the links in the email are clicked, the page that loads isn’t LinkedIn. Instead, the user is notified that they are the “5-billionth search.” As a result, they can claim prizes ranging from gift cards to hardware devices. However, before receiving their prize, the user is required to fill out a survey and provide some personal details. More than likely the gift card never materializes.
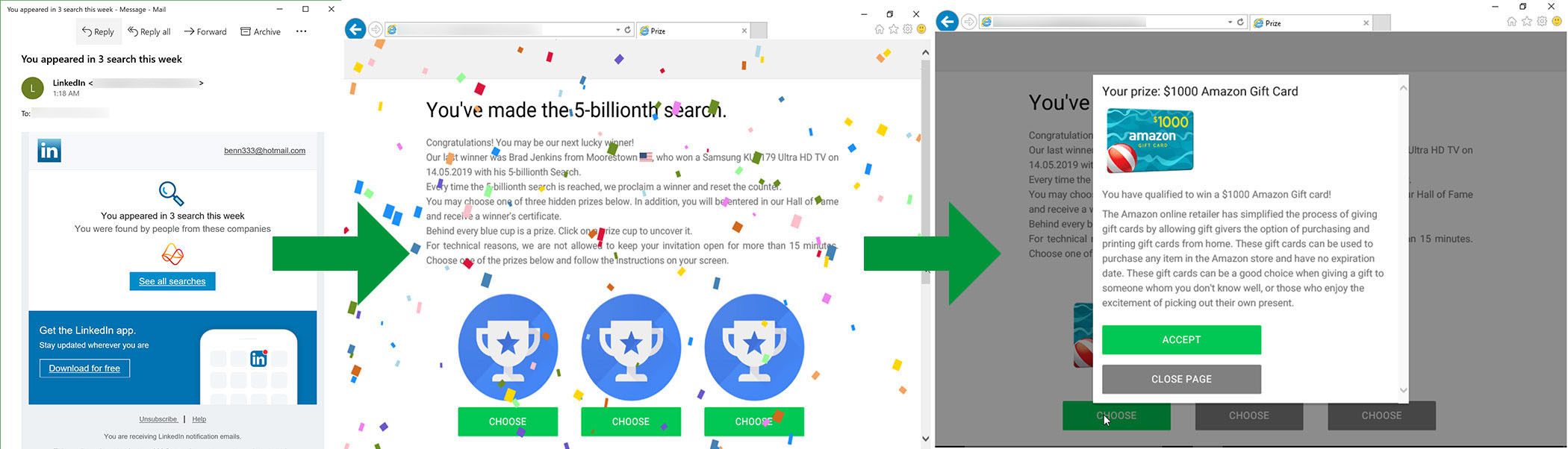
Are they safe?
In each of the examples shown so far, there were indications that some sort of suspicious activity could be taking place. However, there was no smoking gun. Some sites and IP addresses appeared to have participated in past phishing campaigns or other malicious activity. So while these scams may not be performing malicious activity today, there’s nothing to say they won’t be tomorrow.
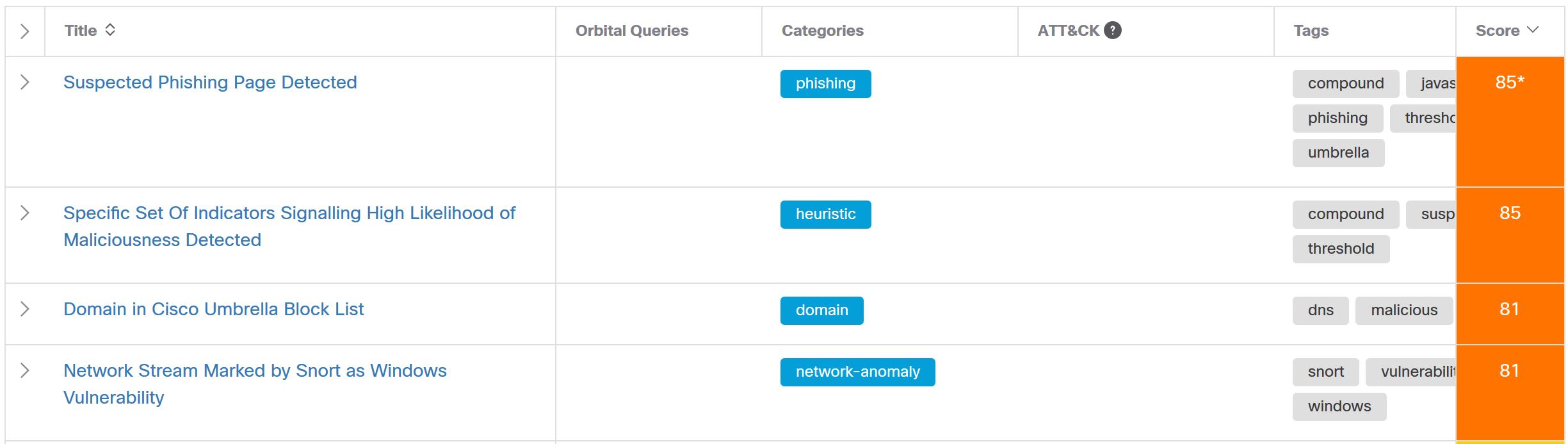
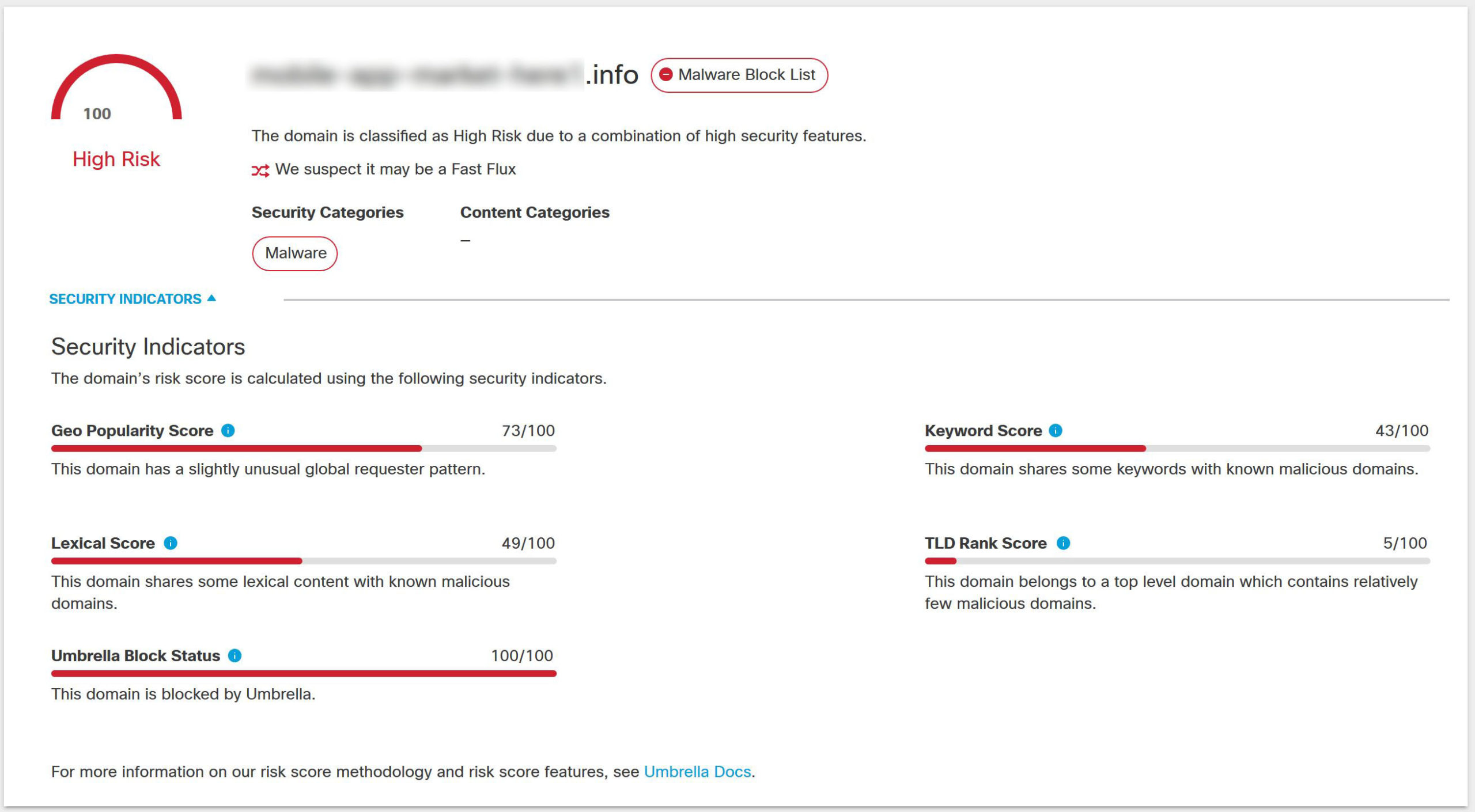
So now that we’ve covered the suspicious, let’s move on to the obviously malicious.
Log in to view
In the following example, the email appears to hint at an upcoming disbursement. While the details are sparse, the idea of unexpected money could lead a curious individual to click. After all, the email simultaneously warns the user that the email is from outside their organization and that it comes from a “trusted sender,” hoping that the recipient will let their guard down.
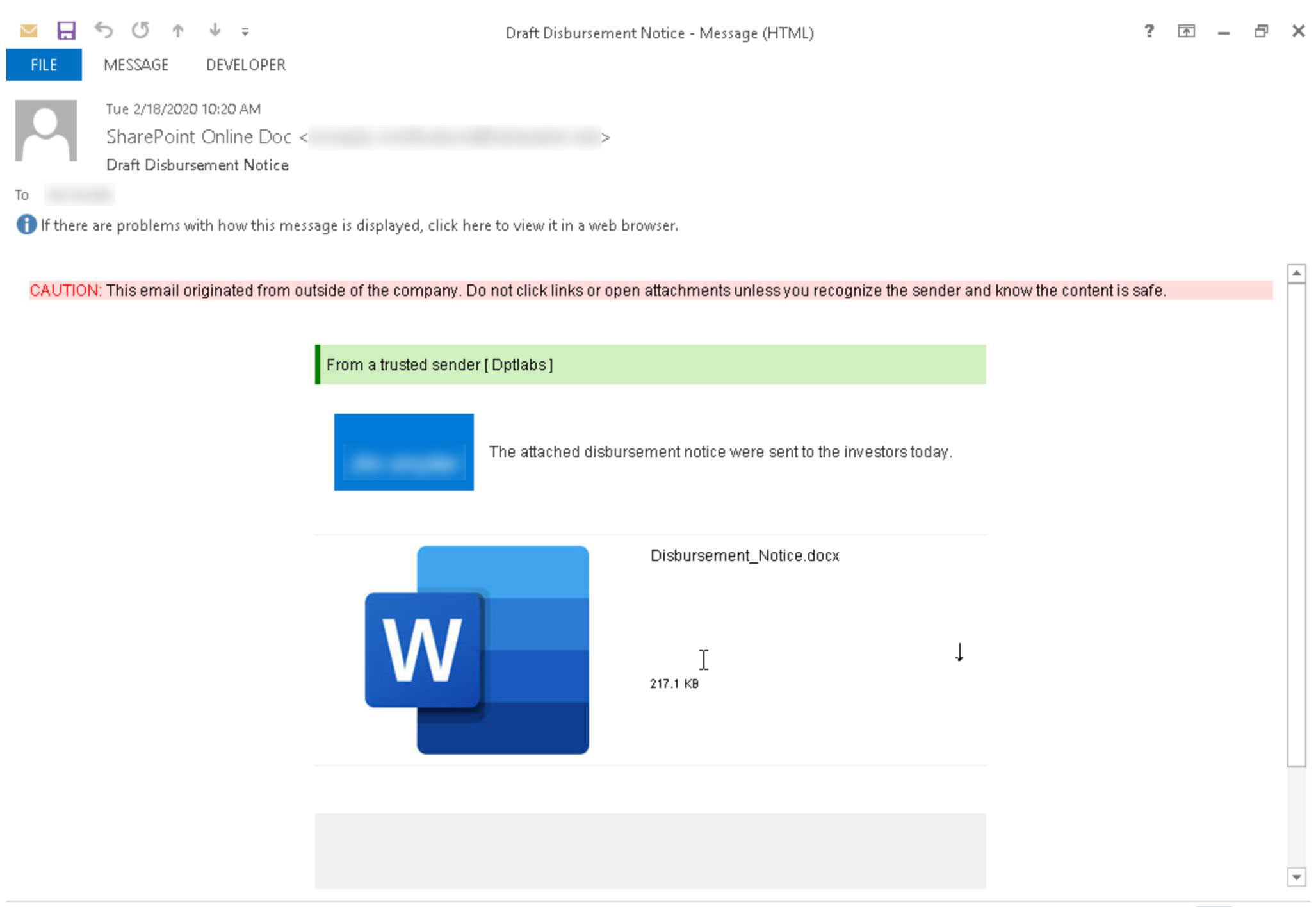
While it looks like the document is attached, the email only contains an image of an attachment. Clicking it does take the recipient to an actual Word doc, hosted on a SharePoint subdomain.
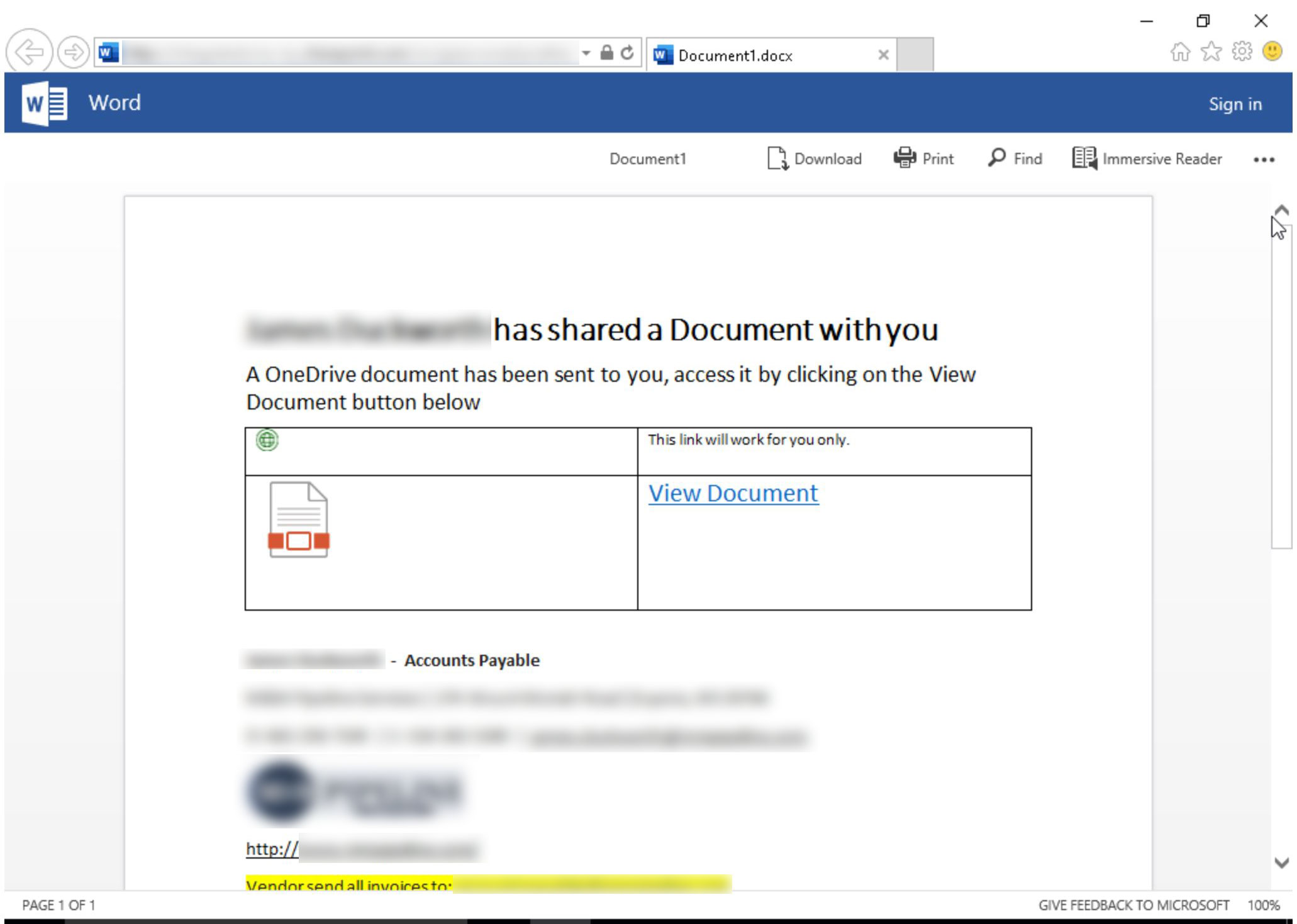
This document contains a link to what appears to be another document. Clicking that link opens another window containing what looks like an Office 365 login page:
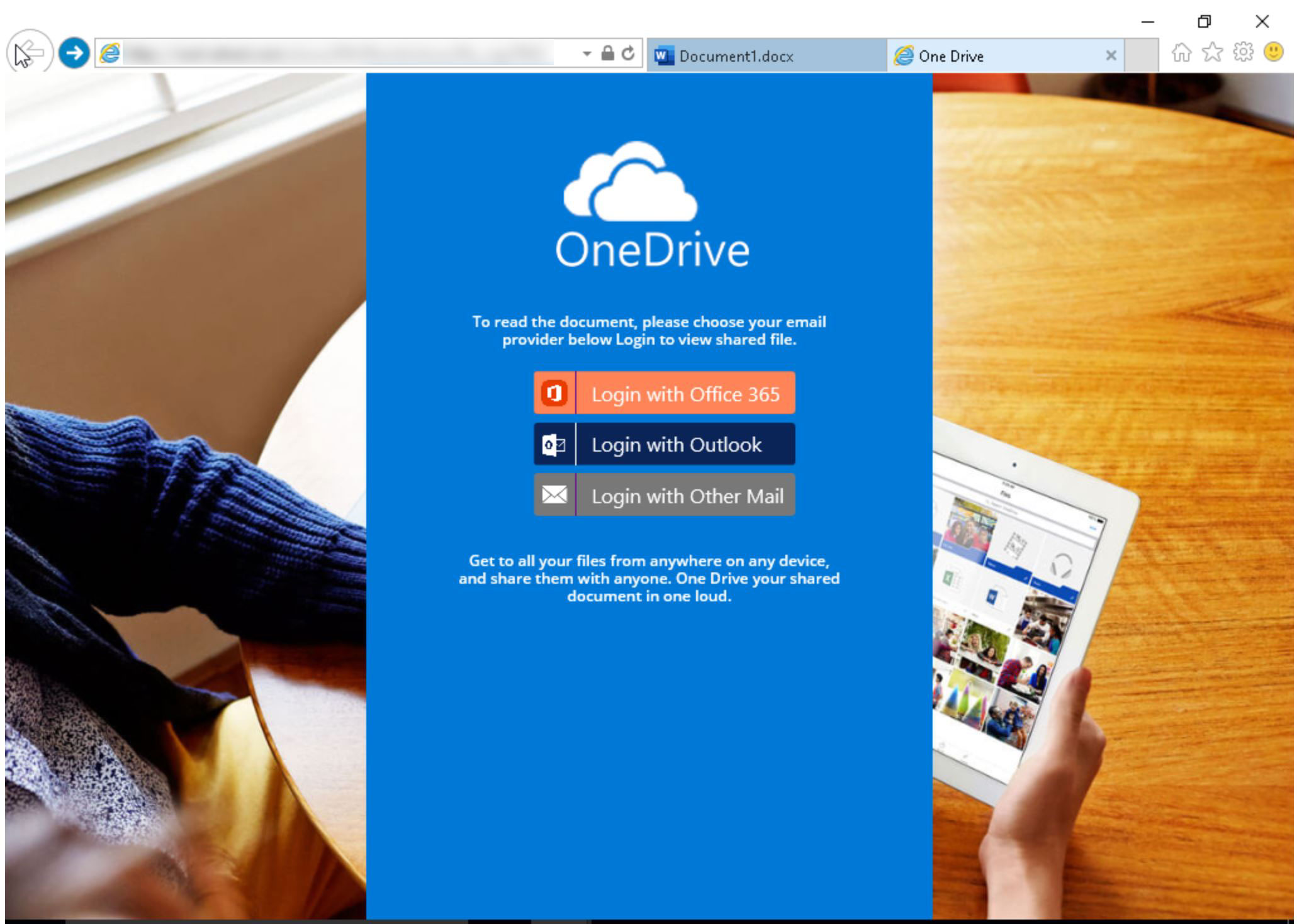
Clicking the first link will take the user to another page that requests the user use their Office login details:
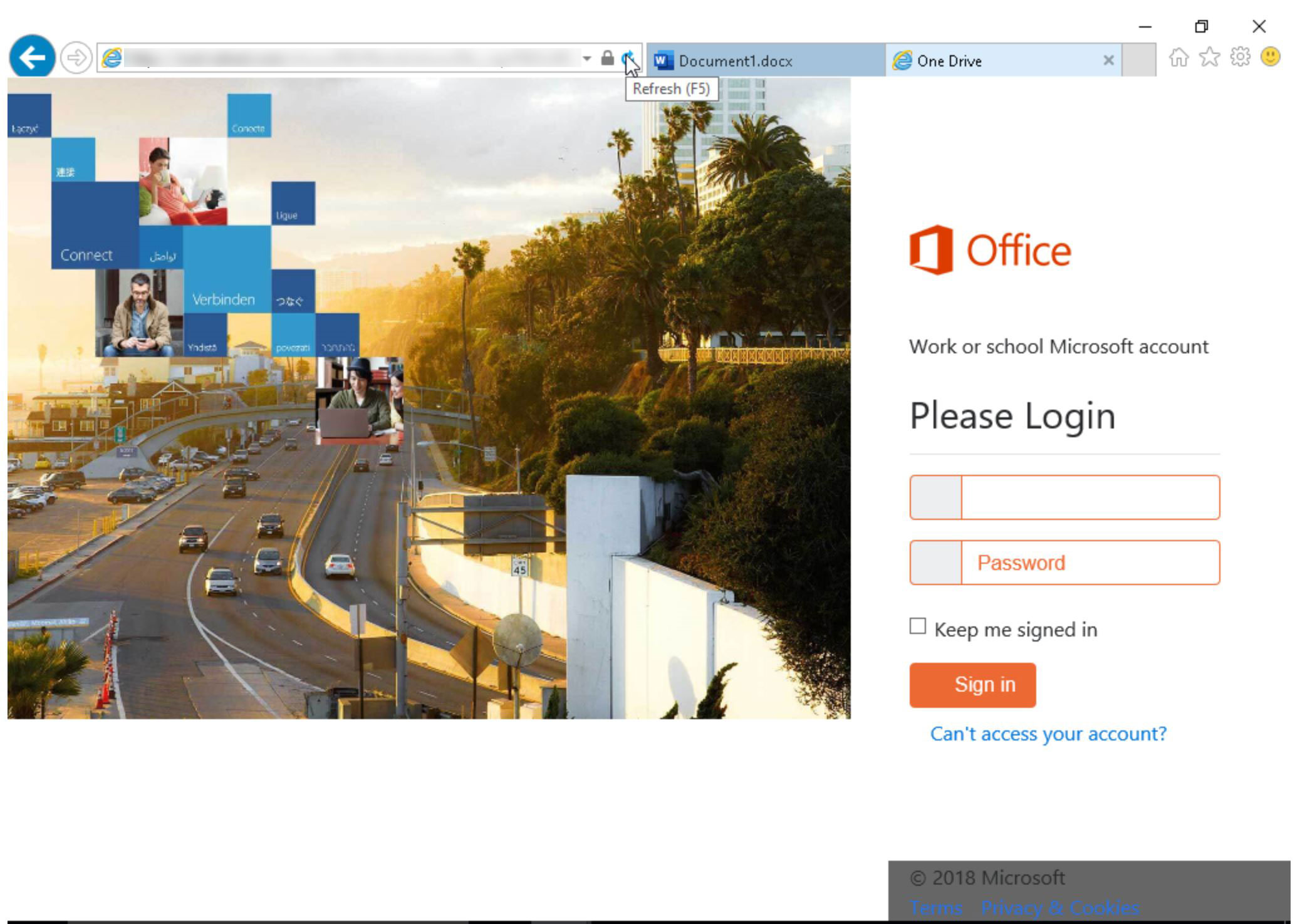
When they click the “Sign in” button, the user is redirected to a legitimate Office 365 page that presents an error message:
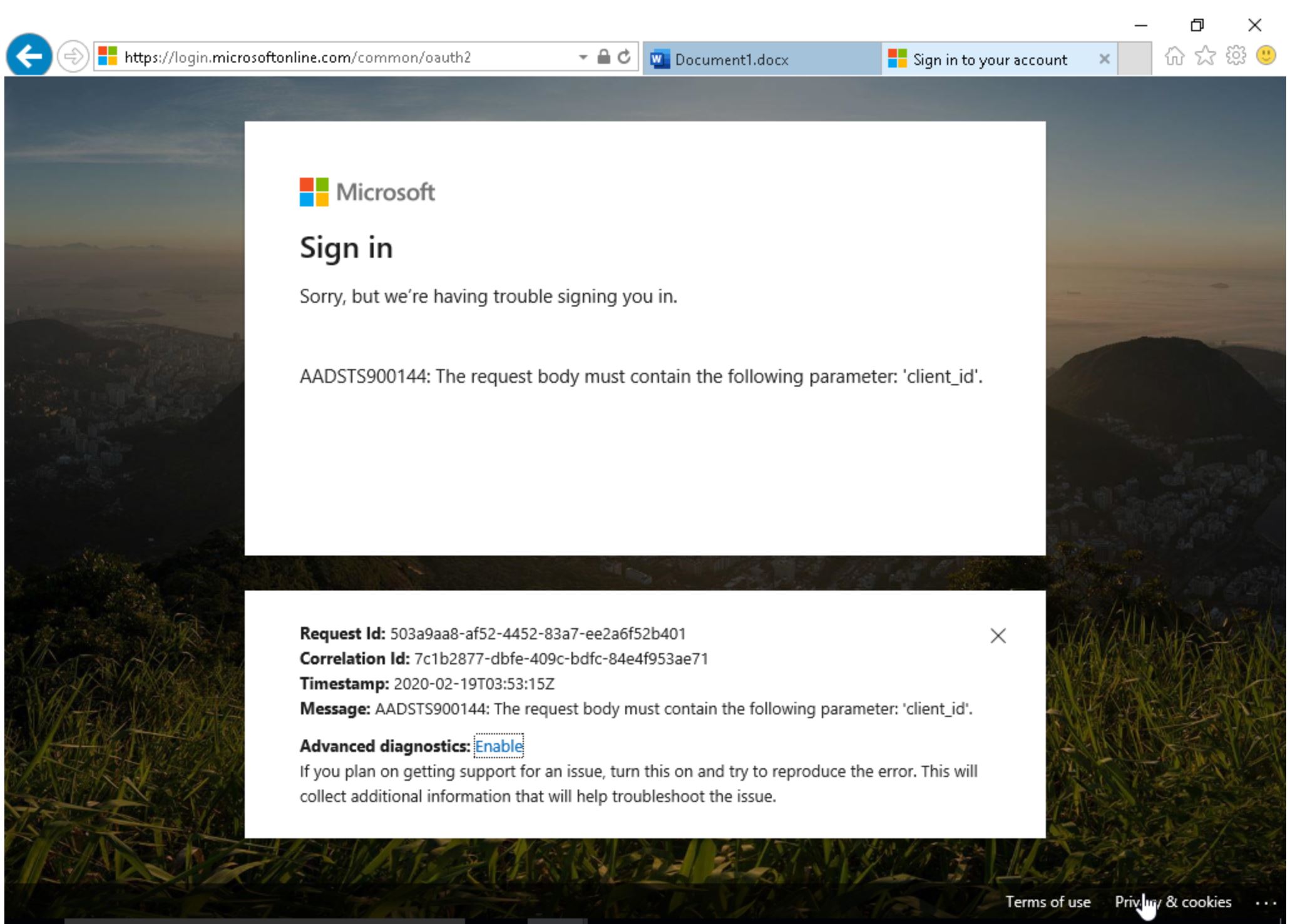
However, login details entered into the previous page have been logged on the malicious site, successfully stealing them from the user.
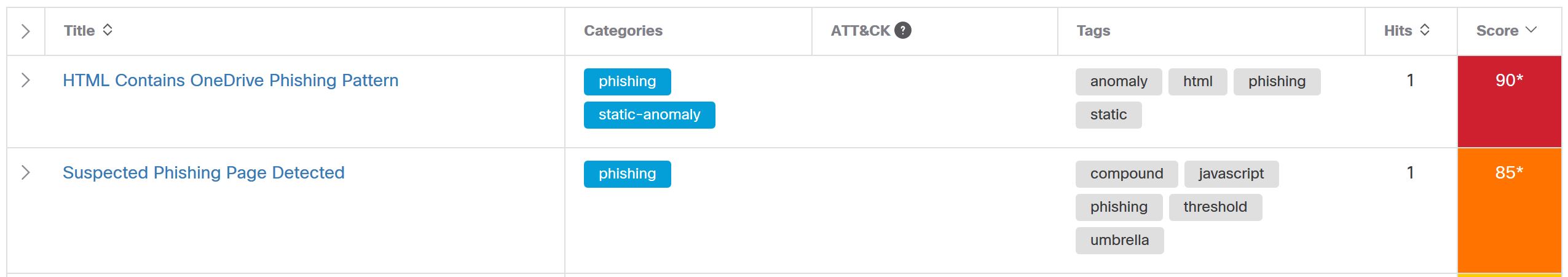
This type of spam isn’t exclusive to Office 365. There are plenty of instances where the bad actors go after other valuable login details, such as those from other webmail accounts, subscription services, or social media accounts.
Package delivery spam
This popular type of spam has proven to be effective enough that it’s used for a variety of objectives. The shipping companies impersonated vary widely and the spam emails are often modeled directly after email notifications you would receive from the actual company.

In other cases, the emails are a little more toned down, arriving as plaintext and including attachments rather than links.
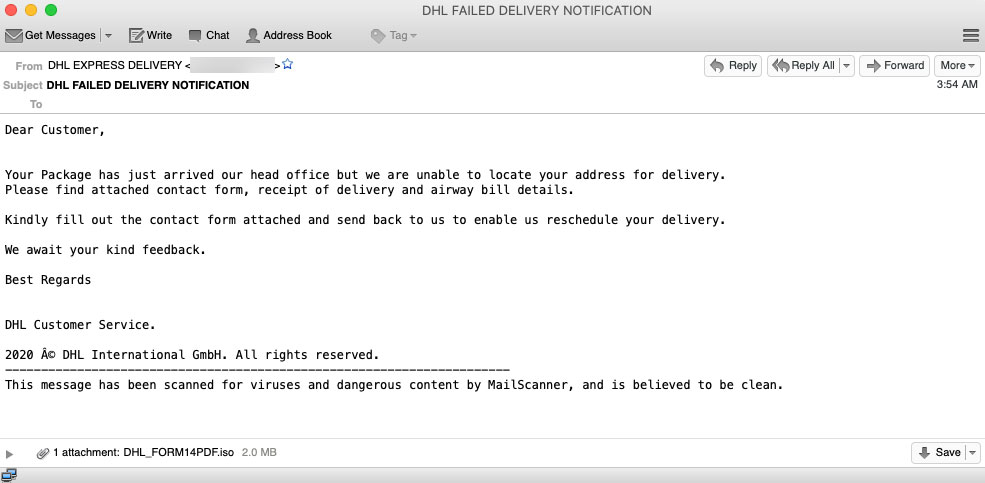
The attached document, if opened, doesn’t show the user the promised contact form. In fact, it doesn’t appear to do anything at all. However, behind the scenes the attachment has compromised the computer with a trojan called “Hawkeye.” This threat is an infostealer that is often used to extract passwords from email and web browser applications, as well as log keystrokes, harvest stored credentials, screenshots, and network activity.
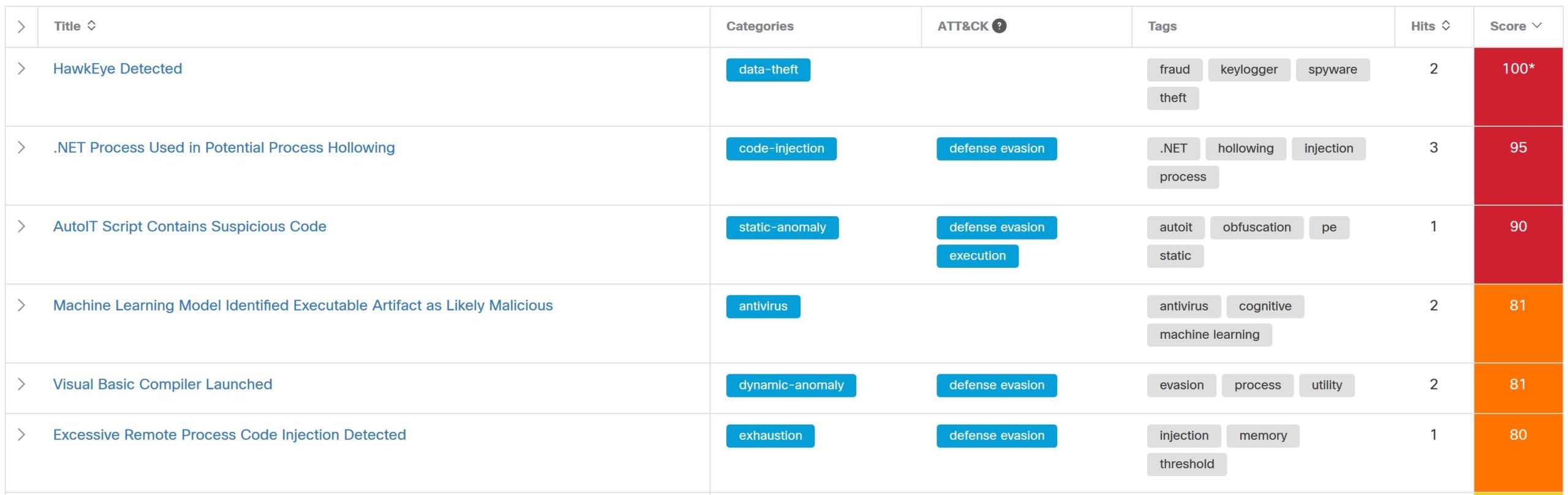
The worst of the worst
The bad actors behind Emotet are one of the largest malicious spam email peddlers these days. We’ve discussed this threat our Defending against today’s critical threats report, and Talos Intelligence has published multiple blogs on the threat. The folks behind Emotet have a few tricks up their sleeves when it comes to email distribution. Their spam campaigns often leverage news headlines and regularly utilize package delivery spam as described above.
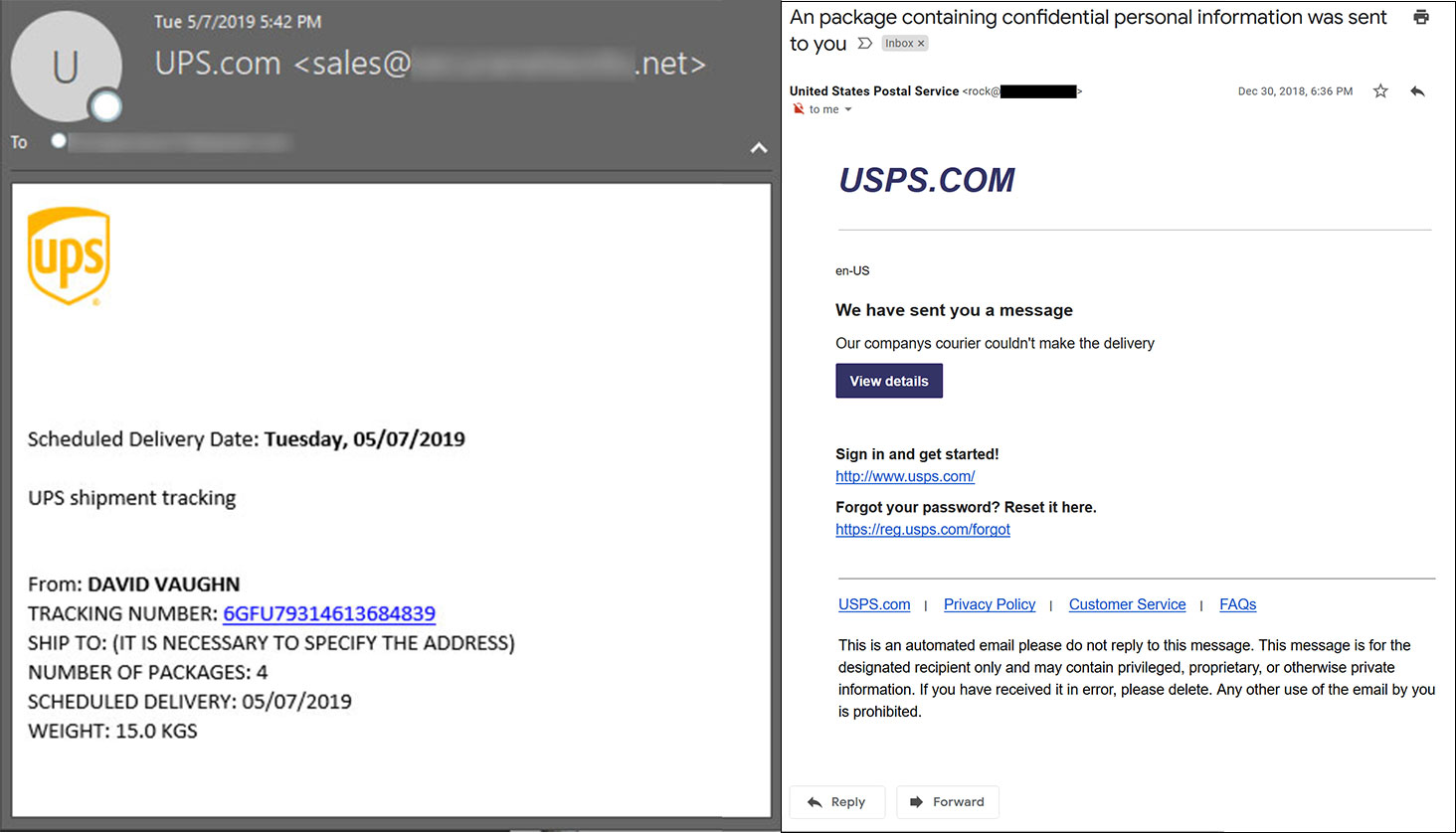
Emotet also often pulls a trick that’s less likely to end up in your spam folder with ordinary email filters applied. These emails often arrive as replies to email conversations you may already be having with someone you know, usually an acquaintance, a co-worker, or an associate in another organization you do business with.
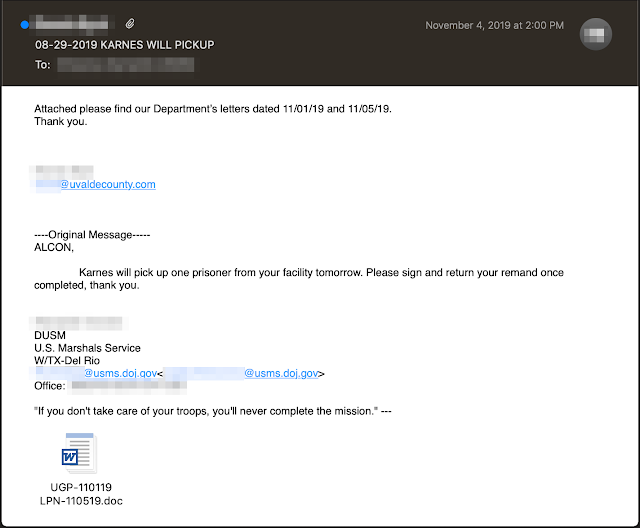
The attachments in these cases, if opened, generally download a copy of Emotet, effectively compromising the system.
How to protect yourself
The simplest way to protect yourself from spam emails such as these is to simply leave them in your spam folder. However, not all spam filtering applications are created equal and sometimes such messages can end up in your inbox—in particular some of the latter examples showcased here. The best thing you can do to identify spam is check for anomalies in the email messages you receive:
- Multiple spelling and grammar errors in emails that appear to come from legitimate organizations should raise a red flag.
- Move your mouse over URLs without clicking them. If the URL that appears at the bottom of the browser window looks at all suspicious, don’t click it.
- Check the From: address. Does the name align with the email address? If not, disregard it.
Beyond the user-based aspects of identifying spam, a layered approach to security is critical in defending an organization from such threats.
Spam filtering software for email is critical. Deploying a robust email threat defense like Cisco Email Security that utilizes URL blocking capabilities and Advanced Phishing Protection’s machine learning to understand and authenticate email identities and behavioral relationships filter out spam emails and prevent attacks.
Endpoint protection software can also assist in detecting and quarantining malicious attachments. Cisco AMP for Email Security defends your business against such threats. Not only that, but AMP analyzes emails for threats such as zero-day exploits hidden in malicious attachments. It gives you advanced protection against spear phishing, ransomware, and other sophisticated attacks.
Tools for dynamically sandboxing threats, such as Cisco Threat Grid, can be used to analyze threats in a safe environment. Even better, integrate sandboxing so that it happens automatically in the background for new files and URLs arriving in email to quickly understand if they are malicious.
Finally, solutions such as Cisco Umbrella can not only block access to malicious sites, stopping many threats in their tracks, but additional tools like Umbrella Investigate provide further threat intelligence around a URL, domain, or IP address to better understand the sites your organization comes in contact with.
Enjoyed reading this Threat of the Month? Subscribe to the Threat of the Month blog series and get alerted when new blogs are published.


Great share!