These days there are so many initiatives for cybersecurity and digital transformation across Federal Government that it’s getting hard to keep up, let alone figure out how to implement them all. But by adopting Zero Trust as your agency’s operational paradigm, you can chart a principled approach to network architecture and security. And in doing so, create a new “way of life” for your network. Let’s take a deeper look on what that means for your agency.
Digital transformation and changing cybersecurity essentials
There is an ever-growing need in government for users and applications to access, share and use digital information to support data-driven outcomes, make decisions and implement AI/ML algorithms to enhance productivity and mission success. That’s why, in its 2018 Artificial Intelligence Strategy, the Department of Defense (DoD) recognized the need to “put in place key building blocks and platforms to scale and democratize access to AI”. This includes creating a common foundation of shared data, reusable tools, frameworks and standards, and cloud and edge services. As a result, we need to accept that data democratization is fundamental to digital transformation.
However, there’s also the need for tighter security controls that necessitate continuously validating and improving the security posture of a network. This should include ensuring the compliance of devices connected to and applications running on the network. A good example is the National Defense Authorization Act for Fiscal Year 2017, Public Law 114-328, § 1653. It directed the DoD to implement automated capabilities for Information Security Continuous Monitoring (ISCM) and Comply-To-Connect (C2C). Likewise, the Department of Homeland Security (DHS) has developed the Continuous Diagnostics and Mitigation (CDM) program to bring multiple frameworks and strategies together.
In addition, many Federal policies refer to appropriate NIST Special Publications like 800-137 (ISCM), 800-53 (Assessing Security and Privacy Controls), 800-63 (Digital Identity), 800-82 (ICS), and 800-171 (CUI). These are helping agencies apply the appropriate privacy, risk and security frameworks and controls to secure their data. And most recently, the DoD codified several of these standards and guidelines in a single framework called the Cybersecurity Maturity Model Certification (CMMC). It’s helping enhance protection of controlled unclassified information (CUI) within the Defense Industrial Base.
The National Institute of Standards and Technology (NIST) has also released its second draft Zero Trust Architecture publication (NIST SP 800-207). You can check out this blog for a quick overview.
Zero Trust is a deliberate lifestyle choice
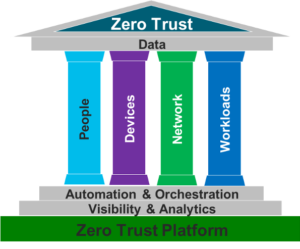 Clearly, there are many policies, guidelines and standards that drive cybersecurity. But until now, we’ve been missing an operational paradigm on how we can implement them all while simultaneously accelerating Federal digital transformation to enhance mission success. On the one hand, Federal agencies must provide unfettered access to data for digital transformation. On the other, Federal CIO’s/CISOs must safely apply authentication and authorization of both user and device to that data. But these needs no longer have to conflict. Data democratization can exist simultaneously with data security and data governance.
Clearly, there are many policies, guidelines and standards that drive cybersecurity. But until now, we’ve been missing an operational paradigm on how we can implement them all while simultaneously accelerating Federal digital transformation to enhance mission success. On the one hand, Federal agencies must provide unfettered access to data for digital transformation. On the other, Federal CIO’s/CISOs must safely apply authentication and authorization of both user and device to that data. But these needs no longer have to conflict. Data democratization can exist simultaneously with data security and data governance.
Adoption of Zero Trust as an operational paradigm is a commitment to changing the how you think about and how you approach and implement cybersecurity defenses and network operations. But Zero Trust is not something you buy. Instead it’s a deliberate commitment to a principled approach to network architecture and security. More importantly, it’s committing to a deliberate “way of life” for your agency’s network.
The Zero Trust fundamentals
Essentially, a Zero Trust operational paradigm means that security and networking always form a symbiotic pair:
- Security is ever-present, enabling organizations to reduce risks to their network and data.
- The network securely makes agency data and resources available to only authorized users—each and every time access is requested.
With Zero Trust, verification is conducted before access is granted (regardless of who or what is trying to access network data or resources). Basically, trustworthiness must be verified before gaining access to data or a resource.
In order to prevent unauthorized access to data and resources, access control enforcement must be as granular as possible. So, the four basic questions asked by the DHS CDM program must always have answers each and every time an access decision or resource request occurs:
- What is on the network?
- Who is on the network?
- What is happening on the network?
- How is data protected?
Likewise, for DoD C2C we must have answers for these questions:
- Does the user have the appropriate authorization to access the network?
- Are the devices being utilized in compliance with agency regulations and policies?
- If they’re not in compliance, how should the endpoint be quarantined while it is being remediated?
So, how do I start on this journey?
The first step of just committing to this journey does not have to be challenging. Fundamental identity management, device management and event logging are necessary entry conditions. Establishing a Zero Trust Architecture is often possible by starting with many of the technologies that an agency probably already has; and leveraging the process steps already taken in 800-37 and RMF (knowing assets, users, data flows and workflows). As shown in the NIST diagram below, the integration of that identity knowledge and the multiple data sources and policy rules forms the necessary inputs for an access/resource policy decision to be formed in the network control plane and be implemented in the network’s data plane.
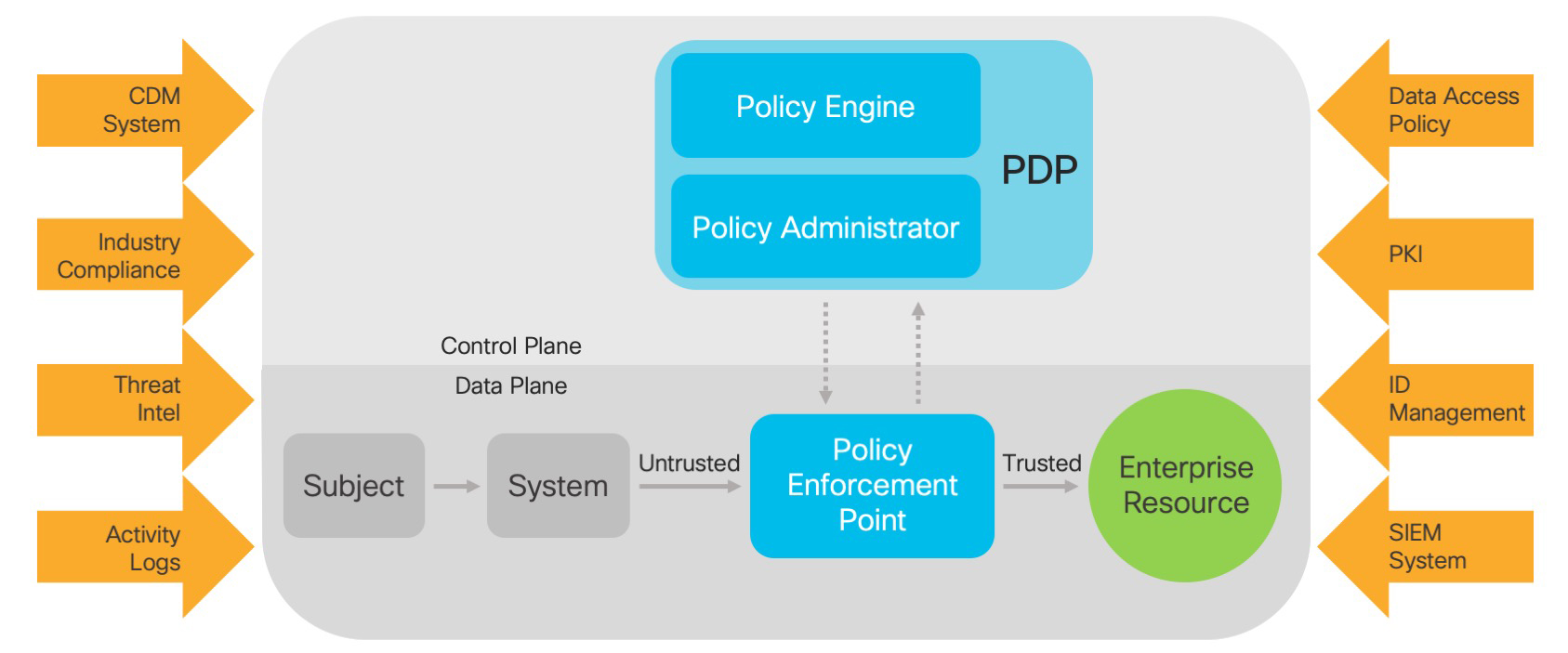
Taking this approach means committing to an expanded, more abstract notion of what identity means for the network at the moment of authentication and authorization. Of course, it certainly must include criteria described in NIST 800-63 and associated agency standards. However, in order for the Policy Engine to make sound access decisions, as much context about the user, device type, health of the device, network location, application type, digital certificate, etc. must all be continuously included and evaluated for identity of the “subject” (combination of user / device / application) for authentication and authorization.
The risk characteristics of type of data or resources that are being accessed drives the policy formulation to allow (or reject) the “subject’s” access. This is based on policy in relation to the subject’s identity. It’s especially important for agencies that have identified high-value assets and are applying stringent NIST 800-171 controls to identify and authenticate users/systems/components before establishing a network connection. This should be done by using enterprise-issued credentials and technologies, like 802.1x, to restrict the connection of unauthorized or misconfigured assets. Relying solely on unauthenticated information to grant network access (like solely based on network MAC addresses without additional device and/or network context for Identity) should not be allowed when living the Zero Trust lifestyle.
Going beyond the basics
The Zero-Trust model of security prompts you to question your assumptions of trust every time there’s an access event. Committing to this operational paradigm means implementing the means of sharing dynamic context on identity, vulnerability and threat associated with users, devices and applications across all network enforcement points. Done correctly, a ZTA approach improves the efficiency of daily network operations.
Many Federal policies and cybersecurity initiatives support the adoption of a Zero Trust Architectural approach. Making a deliberate commitment to a Zero Trust operational paradigm will reinforce an organization’s security posture while simultaneously supporting Federal digital transformation.
Cisco was recently named a leader in The Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019
– read the report to learn more about our market leadership in current Zero Trust offerings and strategy.
Register today for our latest Webinar
Controlling chaos: Are you prepared for your next breach?
Date: April 21, 2020
Time: 1:00PM – 2:00PM EST
The finish line for every IT security team is Breach Defense: keeping attackers from accessing devices and data. But there is never enough time to respond to every alert and simply understanding what has happened, or should have happened across your security tools can take hours. In this webinar you’ll see how Cisco can help your agency leave those challenges behind.
Resources
Read more about Zero Trust 101 and its importance for Federal Digital Transformation in our latest Cisco Whitepaper: Zero Trust 101: Enabling Your Agency’s Mission

CONNECT WITH US