I am writing this blog as the 2014 recipient of the IEEE Women in Engineering Region 8 Clementina Saduwa Award named after an amazing woman whose life was cut short in 2007. On a personal level, I am extremely passionate about the possibilities that technology presents for young girls and aspiring women. As a CTO for Cisco Services, my own role is concentrated on the use of technologies to develop architectures that will delight our customers. Why is technology interesting to me? It’s what one can do with the technology as an enabler to solving problems and to creating opportunities.
I became interested in technology because of my curiosity and encouragement from wonderful individuals who helped pave the way for me. My personal career highlights are numerous where risk taking and passion for making a difference in this world are common attributes. Our world needs young girls to create their own career path in Information and Communication Technology (ICT). A career in technology can be fun!
My mother was role model and encouraged me to be the person I want to be. Coming together to solve a problem and to create opportunities – we can rise above gender discrimination – but it’s about being bold in the process and having the courage to do so -make no doubt about this fact. I dream of a society where such a topic is no longer an issue but so engrained in our DNA !
What is Cisco doing?
Cisco has been very active in the ITU’s Girls in ICT initiative, where girls from secondary schools or universities are invited to spend the day at the office of ICT companies and government agencies so they better understand the opportunities the ICT sector holds for their future see.
ITU will have a live webcast on April 15 2014 at 12:30 CET.
Cisco wants to encourage girls to consider ICT as a valuable career option. We understand the value of diversity in the workforce and it is our aspiration to build a gender -balanced workforce. At Cisco, two of the top technology positions are held by women: both the Chief Technology Officer (CTO) and the CIO (Chief Information Officer) of Cisco are female. “If you cannot see it, you cannot be it!”
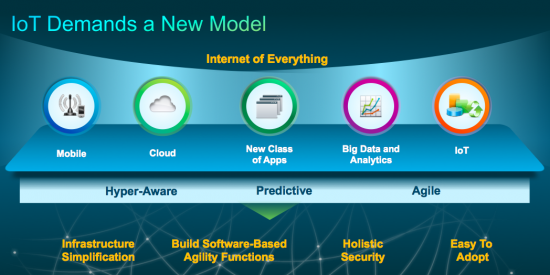
At Cisco, we take our commitment to making ICT career opportunities open to all seriously. We understand the value of a diverse workforce and believe that many more girls would pursue careers in ICT if they were better informed about the many different types of jobs available within the sector. By 2020 there will be approximately 50 billion things connected to the Internet. At its essence, the Internet of Everything is the networked connection of people, process, data and things…and is set to create an unprecedented level of disruption across industries, globally.
In fact, Cisco offices around the world are getting ready to host #GirlsInICT Day 2014! Girls to create ICT jobs of tomorrow #STEM #GirlsInIC
Further Continue reading “Why Information and Communication Technology (ICT) Matters for Girls”
Share:



 “The Mighty Middle.” That’s what we call the world’s midmarket companies. According to
“The Mighty Middle.” That’s what we call the world’s midmarket companies. According to
CONNECT WITH US