Stop-think-connect is not only for kids. Everyone, including nerds like me and network and security professionals, should pay more attention before connecting any device to the Internet. Routers (wireless and wired), industrial control systems, video surveillance cameras, fire alarm systems, traffic cameras, home and building automation systems, and many other devices are being connected to the Internet every single day, wide open. If you don’t believe me do a quick search on SHODAN.
Tons of articles and presentations have been created about SHODAN, so I will be brief. SHODAN was created by John Matherly and it is often called “the Google of the hackers.” Machines scan the Internet looking for devices that folks have left unsecured (often with default usernames and passwords and other times with no passwords at all). Project SHINE, which has been scanning SCADA/ICS devices from SHODAN, appears to be discovering around 8,000 new exposed devices each day.
A very large number of small (and not-so-small) businesses have devices with Samba shares, telnet services, FTP, etc., wide open on the Internet with no authentication whatsoever.
Numerous systems are still using telnet (yes, telnet) without authentication. According to John Matherly, “there are more telnet servers in SHODAN than HTTPS servers.” Many video surveillance cameras, fire alarm systems, and traffic cameras are completely exposed.
“Friends don’t let other friends do this…”
Attacks are getting more targeted. Information about you and your organization is more readily available than ever before. In the past few months, new attack techniques have been noticed. However, a lot of the same attack methods used in the last couple of years still continue to be successful. Why use complicated and sophisticated methods if attackers can just refine their old strategies?
If you take a look at SHODAN, many people have saved search strings such as: router default password, cameras , admin+1234, phpMyAdmin, ArduinoWebserver, netcam, scada, admin/admin, cisco/cisco, sip gateway, and many more.
Why are SIP gateways wide open on the Internet with no password and allowing methods like INVITE, ACK, BYE, CANCEL, PRACK, INFO, SUBSCRIBE, NOTIFY, REFER, UPDATE, MESSAGE, and PUBLISH?
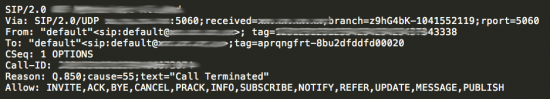
INVITE, ACK, BYE, CANCEL ,and PRACK are used for making Voice over IP (VoIP) calls. SUBSCRIBE and NOTIFY are often used for unified communications presence features. MESSAGE and PUBLISH are often used for instant messaging (IM). Having all these available methods unsecured is not a good idea.
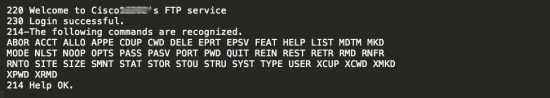
There are many systems that have unsecured FTP services, as illustrated in the following screenshot:
SHODAN has an API with libraries available in Python, Ruby, and Perl that allows anyone to perform creative searches. Several organizations are now using this to confirm that devices in their public Internet IP address ranges are not exposed.
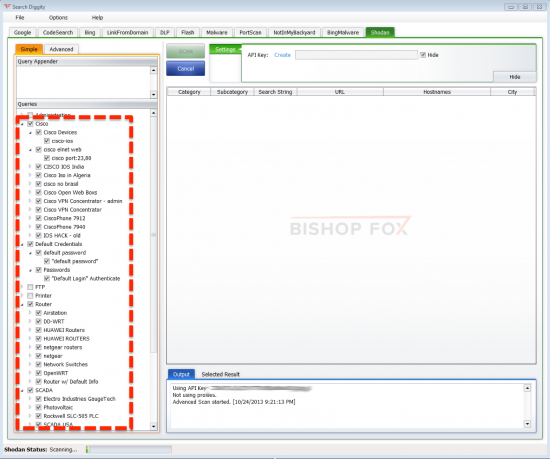
SearchDiggity is another tool that interacts with many search tools including binary malware search, port scans, code search, and SHODAN. Even unsophisticated attackers can get a list of predefined searches for SCADA devices, cameras, Cisco devices, servers, etc.
This is mostly an awareness problem. We (the security community) must take the necessary steps to help others. For instance, HD Moore and Rapid7 started a community effort named Project Sonar with the goal to increase awareness through the active analysis of systems that are misconfigured and exposed on the public Internet. Tools like ZMap, UDPBlast, Nmap, banner-plus.nse, masscares.py, and MASSCAN are being used to generate datasets.
ZMap and MASSCAN are open-source network scanners enhanced to perform Internet-scale network scans. ZMap was developed by Zakir Durumeric, Eric Wustrow, and J. Alex Halderman from the University of Michigan. MASSCAN was developed by Robert David Graham from Errata Security.
In summary, good and bad guys now have very easy capabilities to scan, detect, and compromise your unpatched or misconfigured device. We must continue to engage with others to raise awareness and educate folks about the current threat landscape and help them understand how they can configure their devices in a more secure manner. Steve Martino had a great observation in one of his latest posts:
No organization is ever going to be able to protect 100 percent of its assets 100 percent of the time, which is why I work on the 95/5 principle. No matter how many security solutions are deployed, if attackers are determined enough, they will find a hole. Humans make mistakes and without fail, attackers will take advantage of them.
Most of the earlier examples are based on common sense and very basic best practices. Please help raise awareness and check your own net blocks to make sure that you are not contributing to the problem.


Thanks for this great list of tools. I am increasingly worried about what is being carried inside networks with the staggeringly large number of unpatched devices with issues such as (http://www.saurik.com/id/19)[Yet Another Android Master Key Bug]. Yes, Cisco ISE could help with that. I’ll get right on that; tomorrow.
Hi John,
Thank you for your comment and for reading the post. I completely agree. Insider threat is one of the biggest risk for *any* organization. Insider threat defense needs to be broad because of the physical and logical access to the organization’s systems and intimate knowledge of the organization itself. Patch management is certainly one of the biggest operational challenges and one that leads to many successful attacks/compromises.
Unfortunately, current solutions to the insider threat are largely reactive and tactical; they don’t address the architectural and operational needs demanded by the overall nature of the problem. These solutions and mitigations should involve the full scope of enterprise architecture concerns, including people, processes, technology, and even facilities.
Thanks again!
Omar