Proxy auto-config or PAC files are commonly used by IT departments to update browser settings so that internet traffic passes through the corporate web gateway. The ability to redirect web traffic to malicious proxy servers is particularly attractive for malicious actors since it gives them a method of intercepting and modifying traffic to and from websites from which they can gain financially.
Malicious PAC files have been described since 2005 [1], but this obfuscated example contains a timely festive message. The Portuguese phrase for “Happy Christmas”, “Feliz Natal” is used to encode the IP address of the malicious proxy, 199.188.72.87.
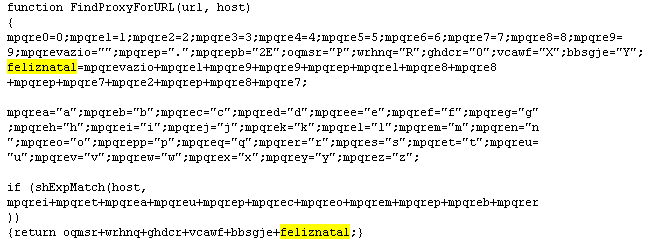
The obfuscated strings contain references to a large set of international and Brazilian web sites ranging from hotmail.com and americanexpress.com to banconordests.gov.br and paypal.com.br. When downloaded the PAC file modifies the browser settings to redirect any request to one of the listed domains to the specified proxy server, 199.188.72.87.
The malicious file named raio.pac, md5 d7b1a0fe59a2dda2fef0bf491cd0968a, is hosted at escoladesampa2divisao.com/luz/raio.pac. However, the PAC file itself does not describe what happens when a victim connects to the proxy while trying to access one of the redirected domains. The proxy may act to impersonate the requested website, or may conduct a man-in-the-middle attack to intercept communications between the victim and the intended website. Given that the majority of the domains listed in the file are those of financial organisations, it’s likely that the individuals behind this attack are seeking to gain access to financial details.
Not all malware is sophisticated. Relatively simple approaches such as the use of PAC files to redirect or intercept web requests are still being used by malicious actors. Network filtering solutions such as the WSA appliance based or the cloud based CWS can block web connections to malicious proxy servers to prevent information loss of information and the facilitation of unauthorised access to financial services.
References.
1. “Malicious PAC script can escalate privilege”, https://bugzilla.mozilla.org/show_bug.cgi?id=321101


Hello Martin,
I’m really surprised to know this loophole as banking system has levels of security to protect from malicious data,How could it possible can elaborate more.I want to do research on this.
Hi Raj,
Thanks for the comment. My guess is that the attackers are either looking to conduct a Man-in-the-middle attack(http://en.wikipedia.org/wiki/Man-in-the-middle_attack), or they’re looking to replace the legitimate website with a similar looking fake phishing site (http://en.wikipedia.org/wiki/Phishing)
Hope this helps,
Martin
I wrote about snort detecting this sometime ago. Sure Sourcefire could detect this too and now Cisco product =)!
http://blog.spiderlabs.com/2012/03/detecting-brazilian-trojan-bankers-with-snort-http_inspect.html
Regards.
Thanks for the comment. There are many different techniques and products to detect and mitigate against such threats. The important thing is to ensure that you have many layers of protection to make sure that you are catching these threats before they cause harm.
My son was recently trying to explain malware to my mother and I. I’ve been trying to do some research on my own and it is definitely scary stuff. How can we protect ourselves? My son said some of the anti-virus programs actually cause more problems and don’t help with situations like this.
Hi Anne. The important thing is to be aware of what you are protecting and the consequences of not protecting it. For a home computer, I’d recommend making sure that you are downloading and installing all software updates, setting updates to ‘automatic’ will take care of this. Keeping software updated minimises the bugs that attackers can use to install malware on your PC.
Sooner or later you will encounter malware, but any reputable anti-virus programme will be able to detect and remove these without any danger to yourself. I wouldn’t recommend browsing the web without having anti-virus running in the background.
Also don’t forget to back up any important files that you may have. Disks can fail without the help of any malware. Make sure that you have your photos, important files and digital music collection stored elsewhere so that you can get them back if your computer were to fail.
Hope this helps, Martin.
With a PAC file, the attackers can be a lot more choosy, redirecting requests to a group of sites or to one site in particular.The attack resembles DNSChanger, the widespread malware that changed a specific file on victim’s systems to reroute all domain name lookups to an attacker-controlled server.
Preventing PAC files from compromising browsers is not a simple task, as client-side security software will likely find it difficult to detect whether a give PAC file is a valid change or a malicious attack.
I agree entirely. I think this is possibly why the attackers chose this technique. This is also a very good example of why it is important to perform anti-virus detection at the network level. Appliances such as WSA can detect these files while they are in the process of being downloaded, but once the malware has modified the victim’s browser they are much more difficult to detect.