One of the key challenge’s businesses face is how to provide a secure infrastructure for applications without compromising agility. With the rise of cloud usage, containers, and microservices, many companies choose microsegmentation as the means to protect critical applications from compromise. Choosing a proactive approach to security to build upon their existing perimeter defenses.
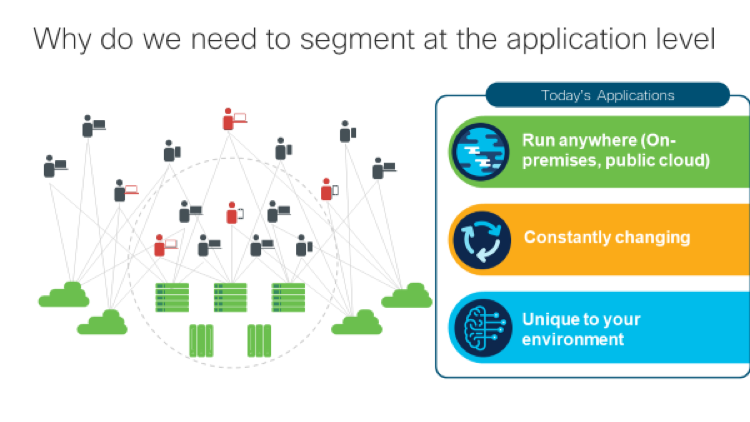
Microsegmentation refers to a method of securing multi cloud data centers using granular segmentation rules for the individual workload or application, reducing the risk of an attacker moving from one compromised workload or application to another. It can be thought of as an evolution of traditional firewall style controls to support hybrid cloud, containerized environments.
This granular control means communication can be expressly allowed between specific parts of an application and all other communications denied by default, commonly referred to as a zero trust model. As a result, the data center is significantly hardened as attackers cannot move from one compromised application or workload to another.
Microsegmentation sounds great in theory but real-life implementation is challenging. A successful microsegmentation project needs to begin with a thorough discovery process to map data flows on how applications, services, and systems all communicate with each other. Visibility is critical at this beginning stage of the microsegmentation journey.
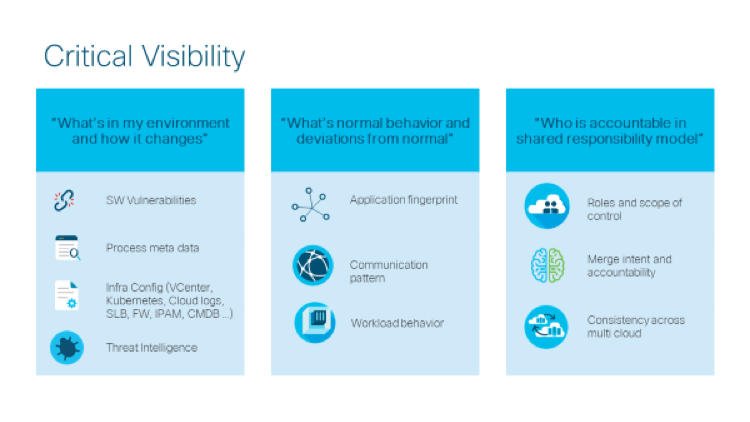
Locking down application workloads without a deep, thorough understanding of exactly what communications are taking place and how data is flowing could result in failures and outages which will stall or result in the cancellation of the microsegmentation project all together.
Once a baseline or application dependency map is created with the application components, communications, and dependencies, then a business can begin the process of generating and enforcing microsegmentation policies. In todays’ threat environment its not enough to be aware; it’s important to move to active protection through consistent policy enforcement across the multicloud infrastructure.
One challenge in the microsegmentation journey is relying on a manual process to map application flows and determine what segmentation policies should be put in place. Manual processes don’t scale to meet the needs of today’s business with the complexities of today’s applications and workloads.
What’s needed is an automated process for policy generation and enforcement that leverages application behavior based on workload context and machine learning to recommend microsegmentation policies based on the specifics of the environment. An automated policy that also includes insights from existing security policies based on business needs plus leverage information from 3rd party sources. Automation also shortens the length of deployment time for the microsegmentation policies. Without comprehensive visibility and automation many microsegmentation projects fail.
Microsegmentation is not a “one and done” project, but a journey. Applications, workloads, and their environment are constantly changing. Automation is important to ensure your microsegmentation policies are kept up to date as application behavior changes and to track compliance to identify deviations quickly.
Microsegmentation is an important step for businesses to protect their applications. For more information on successful microsegmentation with Cisco Tetration, please watch:


CONNECT WITH US