Our Common Platform Architecture (CPA) for Big Data has been gaining momentum as a viable platform for enterprise big data deployments. The newest addition to the portfolio is EMC’s new Pivotal HD™ that natively integrates Greenplum MPP database technology with Apache Hadoop enabling SQL applications and traditional business intelligence tools directly on Hadoop framework. Extending support for Pivotal HD on Cisco UCS, Satinder Sethi, Vice President at Cisco’s Datacenter Group said “Hadoop is becoming a critical part of enterprise data management portfolio that must co-exist and complement enterprise applications, EMC’s Pivotal HD is an important step towards that by enabling native SQL processing for Hadoop”.
Built up on our 3+ years of partnership with Greenplum database distribution and Hadoop distributions, the joint solution offers all the architectural benefits of the CPA including: Unified Fabric – fully redundant active-active fabric for server clustering, Fabric Extender technology – highly scalable and cost-effective connectivity, Unified Management – holistic management of infrastructure through a single pane of glass using UCS manager, and High performance – high speed fabric along with Cisco UCS C240 M3 Rack Servers powered by Intel® Xeon® E5-2600 series processors. Unique to this solution is the management integration and data integration capabilities between Pivotal HD based Big Data applications running on CPA and enterprise application running on Cisco UCS B-Series Blade Servers connected to enterprise SAN storage from EMC or enterprise application running on integrated solutions like Vblock.
The Cisco solution for Pivatol HD is offered as reference architecture and as Cisco UCS SmartPlay solution bundles that can be purchased by ordering a single part number: UCS-EZ-BD-HC – rack level solution optimized for for low cost per terabyte and UCS-EZ-BD-HP – rack level solution offers balance of compute power with IO bandwidth optimized for price/performance.

For more information see: Cisco Big Data SmartPlay Solution Bundles and Common Platform Architecture (CPA) for Big Data.
Cisco UCS Common Platform Architecture Version 2 (CPA v2) for Big Data with Pivotal HD and HAWQ
 This six-part series focuses on
This six-part series focuses on  The method to the madness. Let me take you on a short mathematical journey using the figure below. Starting at the top, we know each E5-2665 processor has a SPECint of 305. It doesn’t matter how many cores it has or how fast those cores are clocked. It has a SPECint score of 305 (as compared to 187.5 for the E5-2643 processor). Continuing down the figure below, each blade we tested had two processors, so the E5-2665 based blade has a SPECint of 2 x 305… or 610. The E5-2665 blade has a much higher SPECint of 610 than the E5-2643 blade with just 375. And it produced many more desktops as you can see from the graph embedded in the figure (the graph should look familiar to you from
The method to the madness. Let me take you on a short mathematical journey using the figure below. Starting at the top, we know each E5-2665 processor has a SPECint of 305. It doesn’t matter how many cores it has or how fast those cores are clocked. It has a SPECint score of 305 (as compared to 187.5 for the E5-2643 processor). Continuing down the figure below, each blade we tested had two processors, so the E5-2665 based blade has a SPECint of 2 x 305… or 610. The E5-2665 blade has a much higher SPECint of 610 than the E5-2643 blade with just 375. And it produced many more desktops as you can see from the graph embedded in the figure (the graph should look familiar to you from 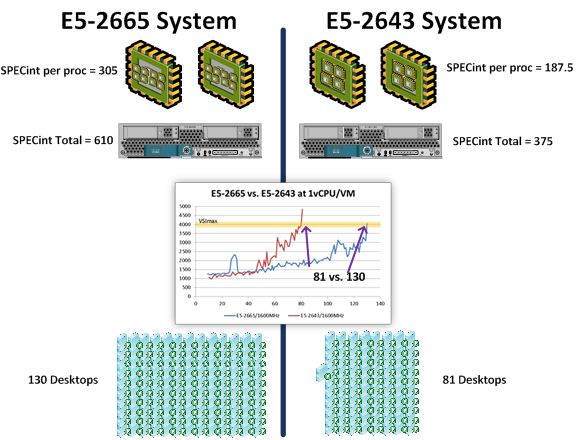
CONNECT WITH US