Retention Trumps Satisfaction
For about a decade, JD Power and Associates has been asking consumers to rate their satisfaction with insurance companies on a simple scale of 1-5. This summer, a study of the auto insurance industry found satisfaction, as measured by this simple survey, to be at an all-time high (2012 U.S. Auto Insurance Study).
Logic might suggest that high customer satisfaction should yield high retention and less price sensitivity, but as is often the case, reality is more complex. It turns out that satisfaction is mere table stakes, and retention is a much more difficult job. Other factors, such as choice of channel and bundling or cross-selling, contribute much more directly to loyalty than this simple score from 1-5 indicates.
In general, today’s consumer wants to use convenient channels such as Web and mobile for simple, low value transactions such as making a payment or updating an address. Those channel preferences shift however, as complexity increases and a more high value interaction with a knowledgeable professional is required. There is very often a point at which a personal, face to face interaction is by far the most efficient way to complete a transaction.
Preferred Channel Service
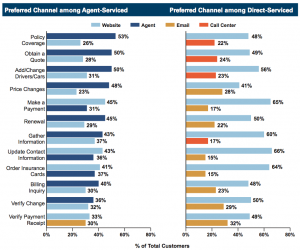 Source: JD Power & Associates, 2012 U.S. Auto Insurance Study
Source: JD Power & Associates, 2012 U.S. Auto Insurance Study
Today’s insurance buyers must choose between a direct channel insurer where the customer experience is based on Web and phone interactions, and the traditional agency channel based on relationship and face to face (or at least one to one via phone) interaction. The gap between these two models is wide. Neither model currently spans the array of channel choice and interaction model necessary to provide both convenience and intimacy. Continue reading “Satisfied Customers Aren’t Necessarily Loyal Customers”




CONNECT WITH US